What Are Sidechains?

Gregory Maxwell is a Bitcoin core developer and Co-Founder and Chief Technology Officer of Blockstream.
Greg was one of the key architects of the two-way peg which makes sidechains possible. He has been a Bitcoin core developer since 2011, and is one of the most active reviewers of cryptographic protocol proposals in the Bitcoin industrial ecosystem.
Blockstream’s sidechains whitepaper showed how multiple blockchains can cooperate and share a currency. In the talk, Blockstream’s CTO Greg Maxwell discussed future cryptocurrency technology that is enabled by such sidechains—security, efficiency and additional features for Bitcoin.
TRANSCRIPT OF What are sidechains?
Thanks. It’s good to see a lot of familiar faces. I find lots of people who’ve been before I was here, come back again to hear this subject. So the first time I’m presenting in front of this group with the sort of block stream add on so it will be interesting to see how that goes. You can tell by the artistically competence audiences compared to my [inaudible 00:00:23]. So I’m going to talk about a couple of things tonight. Previously when I last addressed this group, I talked about some virtual term things, improvements in bitcoin core 011 and I also talked about some more area of philosophical things. Tonight I’m going to talk about things which are both longer term, but also a lot more concrete than philosophical.
So what I want to first do is sort of set a frame work to understand that the work that we’ve been doing here and then talk about what exactly that work is. And a lot of what I’m going to talk about rose out of kind of thinking that occur in this technical space people working in the bowels of the bitcoin protocol. How do we take the system with its design and how we make it scale and adapt, evolve, with greater needs and the wider world. And how do we do that in a way that doesn’t push uncomfortable tradeoffs on the people, who doesn’t change the system against people’s will.
And then pondering that question over many years, some people came up with some interesting answers and then we came up with another problem which is how the heck are we going to build this stuff. Because it turns out solving hard problem sometimes requires a lot of work. So one of the tools that we went to, to try to address that is why I co-founded block stream movement with other technical people from different space as in organizational point to create funding and infrastructure to do some of this really hard long term technical.
So some of these challenges I was going to talk about. I think it’s important to really think about what bitcoin is really set out to do in the world. You think about the traditional systems of value transfer, traditional money systems, they’re based on trust. They’re predicated on trust at all levels and so you have to trust central banks and have to monitor policy, have to trust banks to have good secure accounting. They have to trust people with transport for physical dollars and other assets from one place to another. And these trusts works most of the time, but it doesn’t always work. And whether it’s working or not it’s expensive.
And so this adds friction to the world’s economy. It diverts a large percentage of the world’s GDP to other uses. And I think that that money would be better spent in better other places. So bitcoin has a new idea to address this. The bitcoin says what if we take this trust based system that we use for money all over the world and replace it with machine enforced computerized rules. And then maybe you can make some of these trust issues go away. This is actually fundamentally hard. We try to take information and build the money out of it. We find that information is very different from money. Information can be freely copied. Information is very hard to control. Information doesn’t naturally have owners. We can try to impose ownership on top of it, but those systems really don’t work in a fundamental way. And so how do you go and build a money out of information. How do you go used mechanical rules to build money to our system?
So bitcoin answers that questions. Uses a combination of cryptography and economics to go and build a system [inaudible 00:03:45]. There’s some interesting things in this space. And so we have the result being that we built a system where the rules of the system have true force where it isn’t just that here is the rules and then maybe some people if they like you will follow the rules, but the rules themselves have true forced. Because the algorithm are just enforced inherently by the upper means. So this is great so we can do something interesting and maybe this is useful to the world, maybe it’s a nice alternative.
But the bad news is, is that we built a system where the rules are in charge and this is like sci-fi dystopia rule number one, do not put the computers in charge. There is nothing as infuriatingly stupid as a computer, right. Nothing can be so dumb. But fortunately what we’ve asked bitcoin to do is very narrow. You know, keep track of these tokens in the system. And so bitcoin is not going out and taking over the world fortunately. But the problem that rises is that it’s also not going in doing too much of anything else.
So we were faced with this challenge where if we knew in advance everything that we would have possibly ever wanted bitcoin to do, if we could see all of our problems we could perfectly engineer our systems, make every component right, have no bugs at all. Not just now but against of our needs into the future and we really could have a system that really was just run by the rules and there was no element of trust, no aspect of depending on other people to make it go. But we don’t have that.
We have a world that’s human, right? And we’re limited by what human engineering can do. When bitcoin was first created, the first versions of the system didn’t even enforce ownership. You could spend anyone’s coins because of a bulk and how the opportunities are. So obviously, we couldn’t take bitcoin as it was on day one. It would have been over in 2010 when someone first noticed this. And so it has to evolve. But how do you evolve? So some people have sought to evolve the space of what cryptocurrency does to people by creating new cryptocurrencies with new properties. And this has a number of interesting results.
One pattern I’ve seen a lot is that it seems to have some fairly bad incentives because often the motivation and mechanism stuff is to try to repeat the enormous growth of bitcoins value over time. And so there’s a lot of energy that’s put into the marketing front of the stuff and really not that much energy produce the technologies. There’s been a few alt coins that have done some really interesting technical things, but they are like one-tenth of one percent and the rest are like I copied bitcoin and I changed the name. And that’s not good or bad, it just is. This process has no natural stopping point, right?
Today, we have bitcoin and we have foocoin and we have barcoin and we have bazcoin. And from the public, looking in at this from the outside, why don’t they ask themselves well, why would I use bitcoins. It’s going to be worthless tomorrow because everyone’s going to use barcoin and bazcoin. And so you’ve seen this even with some of the more sophisticated alt coins. They are repeatedly forked over and over again. There is no stopping.
And one of the results of this is that it shakes confidence and this whole idea of making a digital money. And that’s because, really, when we think about why a money-like goods is valuable. It’s valuable because other people will accept it, right? It’s network effect. And splitting it up damages the network effect. In any case, I believe at this point now, I don’t think this is a great way to solve it. It’s a tool. I wish people that are trying out for its luck, but it least not where I would spend my time. So if I’m not going to spend my time making alt coins, what am I going to do, right?
So from the very beginning, bitcoin was designed to be extensible in specific ways. There is a very powerful smart contracting system built into bitcoin from day one that allows users of the system to specify rules for how bitcoins move. What you can do with this is buying bitcoin into larger systems. And so you don’t have to put all features of the world into bitcoin directly. It’s a great idea.
Unfortunately, the original implementation in bitcoin had a bunch of bugs. But it’s possible and there is completely compatible way to fix those bugs and to improve its capability in a smooth way that doesn’t interrupt anyone who doesn’t care about its capabilities.
We use this mechanism called soft-forks, which are backwards extensive – backwards compatible extensions of the bitcoin protocol. We have used them many times before. Most obvious example being the deployment of the three type addresses, P2SH, which is the soft-fork in 2012. But even with the ability to make soft-forks, the backwards compatibly extent bitcoin it’s very difficult to make updates and a production system that people are counting on. That has in, you know, a billion dollars in value or whatever we’re going to be counting each day.
And many technical designs are much easier to do refill. If you have to fit things into the – for a shape that can work as a soft-fork. It’s much harder to design things. So when Adam’s spun back up in the bitcoin space and got really, really involved again, he started talking about this notion of maybe you could extend bitcoin using the concept he was calling the one-way peg. Just you could create a new replacement cryptocurrency network and have it give you coins on it when you earn bitcoins or store bitcoins get coins on new bitcoin. And this could be a mechanism to allow upgrades to the bitcoin system in a way that wasn’t – it wasn’t worth it. You know an upgrade is the old system.
So network effects sort of pushes you over. But this one-way mechanism was a little lame in that you could only go one direction. If it wasn’t clear what direction people wanted to go in if what new – through a multiple new bitcoins which one was the true successor, then that’s not good because you then stop, it makes losers, right? You’ve got some market speculation effect that would be good to avoid.
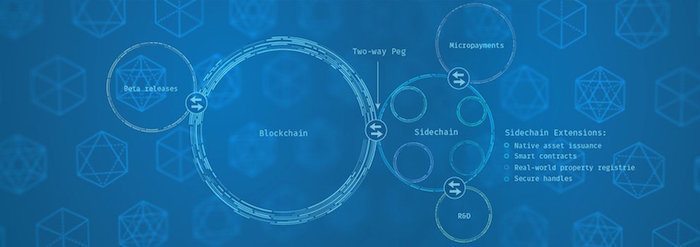
So I added to this in late 2013, a way to accomplish the other direction, the two-way peg. And the idea for the two-way peg, which we’ve described in great depth in the Sidechains whitepaper is to use the smart contracting functionality of bitcoin to ask bitcoin to validate a very particular smart contract. One that says this coin has been handed over to the control of another decentralized network. Whatever that network says do with this coin, then that’s what this coin gets done with. With this mechanism, you can move a coin into another chain, separate fork and then move it back again. You can effectively look at it like it’s freezing the coin in one system and then creating a new one and then restoring it and move back.
So the whole idea of this is to gain freedom, agility of multiple networks without rebooting the network effect. Now we can get all the advantages of being able to switch to, you know, an alt coin or whatever, but still keep the same currency. So we could pace the new risky, experimental, niche features off in separate networks. But unfortunately, making this work requires a great many moving parts. A Lot of protocol design, lot of work about incentives, a lot of details. And it wasn’t stuff you could do in just our spare time. So thus, the company.
So I’m very happy today to introduce a project we were calling the Elements Project in Sidechain elements. And what this is is a project to advance the art of bitcoin, using really no holds bar, right, exploratory technology. And using this [inaudible 00:11:14] concept. So what we’re doing is releasing a piece of free software, MIT licensed based on bitcoin core and publishing to everyone and operating on, enhancing it.
This software has many new and interesting features that I’m going to talk about, some. And it uses the Sidechains mechanism to make – extend the bitcoin ecosystem rather than being [inaudible 00:11:37]. Right now, the initial elements of network is Sidechain called the Alpha. And it is a bitnet – testnet Sidechain. So back in 2010, there’s a parallel bitcoin network that buy social convention a little more has no value. The testnet bitcoin many developers use for it for testing new software. And so we’ve made a Sidechain against testnet and that people use it today.
So outside elements, part of the idea is not just to release the two-way peg mechanism, but to actually put it to some useful because without actual applications for it, it’s just a bunch of cryptographic language, right? What are you going to do with this? This is really useful and so we think so and so we get us some ideas. So when we talk about these features we’ve put into the elements network. And we can think of each one of these features as just – it’s basically one person’s experiment and with a bunch of other people helping out to make it actually work.
And I hope that other people will pick this stuff up and run with it. And I do have the caveat though that the stuff is very raw, right? The whole goal here was to be able to experiment with low risk and that means that we get the benefit of not having to do with much for quality assurance. Right now software in bitcoin core has to be basically bug free.
An elements doesn’t, right? It’s a testing network. So I would suggest people don’t go pick up this code and go use with real value or you may be sorry and I may laugh. So the first of the elements we’re going to talk about tonight is the deterministic peg. This is the two-way peg mechanism that I was just talking about. It allows testnet coins to move into the Alpha Sidechain and back again.
And it has some simple parameters. You start to move in the testnet network, 10 confirms happened on the testnet network, you go tell the Sidechain about it and it takes 144 coins for the various timesout to be met described in detail on the Sidechain whitepaper.
Now although this has this two-way peg mechanism, it is not secure. It is not secure because the testnet network is not too good. The testnet network can be very easily re-organized by anybody with single basic [inaudible 00:14:02]. So it will be interesting to see how this works under adversarial conditions as well. So one thing that comes up while implementing the two-way peg as we described in the whitepaper is that the existing smart contracts language of bitcoin is no longer expressive enough to encode the rules to validate the returning coins.
So what we’re using in Alpha right now is the procedure we described in Appendix A of the Sidechains whitepaper called the federated peg. The federated peg is a centralized mechanism that allows you to experiment with this Sidechains without having to first go and deploy it in the natural network.
So you can think of it as a protocol adapter. Basically, there’s this federation of oracles and N of M threshold. And you show the oracles the contract that you would like the network – the production network to run. But it doesn’t know how to because the smart contracting language isn’t smart enough and if that contract would return true then the oracle sign. So it’s a protocol adapter.
And this means that the participants in this aren’t themselves engaged in any discretion, just mechanically rules. If they misbehave, you can detect it although you can’t do anything about it. You can, you know, stop using that network. As I said there is the security trade-off for it to be decentralized. And if more than a threshold is compromised they can steal alt coins that are entrusted for the Sidechain.
In the case of Alpha, we’re only – we only have to use that mechanism for the direction of the Sidechain back to testnet. The direction from testnet to the Sidechain is directly verified by the Sidechain network. It’s asymmetric like this because we can very freely change the code in the Sidechains. It’s not as easy to change the code in testnet. Although there’s some details of this.
Right now testnet doesn’t have the compact loops that are described in the Appendix B of the Sidechain whitepaper. And so the way it does its verification is by running a separate testnet node alongside the Sidechains node to verify that indeed the move occurred in testnet. And so this work this deterministic peg limitations mostly match design work [inaudible 00:16:15].
So the next element, it’s in the Sidechain elements is Issued Assets. And actually issued assets right now it’s just a full request a depository for this. So in the pipeline, it’s not moving into it at the moment.
So the motivation for the Issued Assets in my mind is that bitcoin brought us these smart contracts which are enforced trustlessly by the network. And this is great because often in the wider world, contracts are dead letters because the cost of enforcement is so high. We have a contract with the paperboy to delivery your paper and he doesn’t, too bad. We’re not taking him to court, right?
So the power of smart contracts is really when network enforces the contract and so enforcement is automatic and it can’t be violated. Since network access [inaudible 00:17:05] enforce the contracts, it’s wonderful and great. Lots of people have imagined doing all kinds of fantastic trustless stuff using smart contracts. But the challenge with that is that the network can only do this trustless magical enforcement for things inside the network. Fortunately, the network cannot reach out into the wider world and change the ownership of physical goods.
And so if you want a smart contract to arbitrate over things other than bitcoin, you need to do something. One way to address that is to represent those other things as assets, as tokens, inside the common network that supports smart contracts. So you can imagine building things like fancy synthetic assets. An asset that is worth some component of bitcoin, some components of automobiles using some smart property concept. But you can’t do that unless the network knows something about it.
So there is this in the space, there’s idea of colored coins which have existed and have been deployed for a number of years. Colored coins have some problems. In general, colored coins are not SPV compatible. They are not compatible with the efficient verification in bitcoin. So it means that the user of a colored coin has to trace the history of bitcoin to the blockchain through all of its owners. Meaning, transferring potentially in 30 gigabytes of data to all the whole blockchains today and only growing overtime. This doesn’t work too well, especially if the user of the colored coins is something like a smart property vending machine or smart property car, or really don’t want your car to have to download the whole blockchain to figure out who owns it.
Colored coins also encourage the creation of a very tiny dust coins transaction outputs in the network that are a growing concern for the overall operating costs for the network. There’s a trade-off with decentralization and cost. The [inaudible 00:18:55] little touchy. And the interest thing is that a bitcoin is valuable so long as the bitcoin network exists and so long as people want bitcoin. But a asset on the network is only valuable as long as the asset exists. It might have a very different lifetime.
And with colored coin, you have no mechanism to say this asset has a different intention policy, different lifetime than bitcoin. And so another kind of assets [inaudible 00:19:19] you could accomplish that. The main problem, though, I think with colored coins is they are invisible to the colorblind network. So either it’s easy to deploy but it also means they can’t be made available to smart contracts like intelligent [inaudible 00:19:32] .
Although there is a big advantage, I think people don’t talk about enough what colored coin is. They could be very censorship resistant because only the parties using colored coin know about the coloration. And if the colored coin system was designed correctly, it could be utterly undetectable to the rest of the network. And so if other nodes network, miners by the censor, colored asset, a well designed colored coin system could avoid that. Although the current colored coin systems aren’t particularly good on network, anti-censorship angle. And so it’s Issued Asset feature.
An elements – what the [inaudible 00:20:06] is that it immediately adds all of the [inaudible 00:20:08] instead of coins it adds the asset-type flat tab. And then the asset type track is used to group the accounting rules in the system. So right now bitcoin protocol enforces rules such as the the sum of input coins have to be less than or equal to the sum of the output coins. So this is just is making sure that the numbers add up, right?
And so these rules can be grouped by asset types to say the sum of input of asset type has to be greater than or equal to the number that come out. Fairly straightforward. And then the issue of the assets, there’s a new special transaction and the TXID, transaction ID of that issuance transaction becomes the asset tag. So this is mostly the [inaudible 00:20:55] and this is all it does right now. But there’s a lot more that you could do and be extended beyond that.
So the next element that’s in the elements network today is this relative check log time verified. So in the original bitcoin systems, bitcoin transactions have a good after date. This is the analog time field. And that’s somewhat useful, but many fancy contracts need something if they are going to hold up. You really want to be able to create scriptPubkeys of the form. Person A can spend or person B can spend the after time X. There’s a BIP65, which is in the works and may be available this year, which adds an absolute check log time for the bitcoin network. And that’s very useful and that’s in the elements, as well.
What relative check log time is is basically taking this a step forward. Instead of saying having a fixed clock, that coin will be spendable after a certain date making that clock relative to another transaction. So the clock can start one transaction and then finish after a gap.
And this is necessary for some fancy protocols like the light coin to give really super scalability. So the way we accomplish this in elements is that in bitcoin there is a 32-bit sequence number for input to a transaction. The original idea was to increment this indicate updated transactions. You could revise a transaction. But there is no enforcement mechanism in the network.
So you can update a transaction within the network to confirm an older version which will probably be not what you wanted and the network might do this because it would be much more profitable to confirm all the version. So because of that people haven’t used replacements in any real capacity in the network because it’s insecure. Because there’s no network enforcement to this convention. You have to basically trust the miners to be honest, which they sometimes are and sometimes aren’t. people aren’t really sure about when they can trust that.
What relative check log time does is it adds rule so that when the sequence number is at its maximum, the transaction can be included at any point. If the sequence number is one less than the maximum, then the coin that it is spending must be at least one block older than the blockchain. If it is two less than the maximum, it must be two blocks older than the blockchain and so on.
And so if you start at the low sequence number and go up, what that means is that the layer version of your transaction will be loadable into the chain earlier than the earlier revisions of your transaction. And so that give us some real consensus enforcement. It’s not a guarantee that the network will confirm the right transaction, but it means the network will have plenty of opportunity where it can only confirm the latest version before it gets to the less recent versions of it. So this is most of the work of Mark and he is also working on proposing this in bitcoin core as well. But it’s available in elements network.
So the next element I’m going to talk about is one that has a kind of exotic name. And it’s name this way to distinguish it from some other words we might use for it. I’ll explain. So the name is Segregated Witness. So if you think about a bitcoin transaction, a bitcoin can be spent whenever some input signature is provided which makes the scriptPubkey return to erase the criteria for spending the coin. The network runs these scripts to verify this is the case and life is happy.
It raises the question, what happens if you take a valid transaction and you take its inputs that are true that you make a script different true and you change them, you change the coding and change the values in it. This doesn’t change what the transaction does. It doesn’t change its behavior. It doesn’t change who it pays. But in bitcoin doing this changes the transaction ID. And it seems like not a big deal, but it turns out to be quite a big deal. For one, it confuses the accounting systems, which is annoying.
But even knowing this, people haven’t made their wallet software handle [inaudible 00:25:05]. So that will be [inaudible 00:25:03]. But more importantly, when a bitcoin transaction spends an unconfirmed coin, it’s dependant on that transaction ID not changing or it will invalidate the transactions. So if you have a chain of unconfirmed transactions, someone going and modifying the signature and one of the early ones invalidates the whole chain all the way down.
And so the obvious thing to say is well, don’t make it possible to do this. But it turns out especially with the expressiveness of script it is really hard to have rules for validating the signature which do not allow the signature to be changed. And in fact cannot be done without reducing some of the flexibility of the script.
There’s a proposal BIP 62 which is rather complicated and it basically says, if you make transactions that fit these narrow set a very common use cases, then we believe that the results with BIP 62 enforced are non-malleable. You cannot change the signature result in another value.
But we’re not even completely sure if BIP 62 is enough. So it’s one of the reasons that BIP 62 is kind of installed. We’ve broken up some parts of it taken and taken it forward into the network. But BIP 62 is a whole – may eventually go in but it’s not a really crisp solution to this problem of malleability.
So the name, where does this name come from? Well, if I talked about segregated signatures it will cause a lot of confusion with that ECDSA cryptographic signatures as well. Bitcoin signature is more than just about crypto part. It’s the whole script validation. It’s the set of inputs to make the transaction true. And so I’m using a bit of jargon here right. Witness it’s a term from mathematical logic. [inaudible 00:26:42] cryptography and what it is is a specific value. It’s a concrete existence proof for a claim. So if I have a function and I say, there is – there exists an X such that F returns true that value X is the witness. So that’s the signature in the transaction is the witness for the transaction.
This is a good way to think about it because bitcoin itself doesn’t care why a transaction was okay. Any valid signature is good enough for the network. The transaction will go through. There’s also is a good reason to think about the way bitcoin works because we know in a fundamental sense that it’s possible to build using fancy cryptographic tools. Systems didn’t allow you to build networks where you can validate their validity without manipulating any of the signature data. It’s the compact proof.
When I say it’s possible that I mean this in a theoretical sense. It’s not at all practical to do that. Yet it may be in ten years, it is. I’m thinking about in terms of witnesses to transactions helps sort of climb the thinking for these systems. And the other thing it’s important about the separation is that, when you are validating, when you are downloading a blockchain, if you do not care to validate the signatures and the all parts of it because you’re just going to trust the miners did the right thing there.
Then you don’t care about the witnesses. You care about the inputs of the transactions because you want to know what coins are being spent and you care about the outputs of the transactions because you want to know which coins are going to be spent in the future. But you don’t care about the signatures, you’re trusting that they’re valid because they’re three years old. And if they were invalid you know, maybe someone will have said something by now.
And right now in fact if you go download bitcoin core it skips verifying signatures deep in the blockchain for performance reasons, because otherwise it take a week or two weeks to synchronize the chain. So it’s a bit of a security trade off the minute it does that. But it still has to transfer the data which is only ridiculous because the witnesses, the part of the transaction you don’t care about if you’re not validating signatures, is two-thirds the data in the bitcoin blockchain.
So all this is to say, well, the obvious solution of this is to take the witness part of the transaction and make it separate to the transaction and you have its witness. The transaction is split into two parts. They are always relayed together. But the transaction ideas [inaudible 00:29:03] which only covers the main transaction part, not any of the signatures.
Now the block itself still needs to commit to the signatures, to the witness. And it does justify adding additional level to the Markle tree to put the hass of the witnesses in. And the reason the blockchain needs to do this is primarily for forensic reasons. You have a two or three multi signature transactions and the coins move, and later you might want to go back and confirm well, who authorized that move. And to do that you need to check to see which of the signatures were actually the one used in the blockchain.
So the result to this separation is it is now possible if you are not checking the signatures in blockchain or not checking all the signatures in the blockchain to not transfer them. And this completely prevents unwanted, unintentional third-party malleability with transactions and it prevents it in a way to assure that it prevents it rather than one we are thinking [inaudible 00:28:23]. So this is mostly the work of [Peter 00:30:01].
So next element I’m going to talk about is some script enhancement. So as I said earlier in my talk, bitcoin script is much more powerful, right. A little too powerful. It have the power to crash nodes and steal coins. So to remove this excessive power many operations in script were disabled which is really just a polite way of saying they’re completely removed. But fortunately, the problems weren’t hard to fix. Unfortunately, they were discovered in an emergency scenario. Instead of fixing them they were removed. They can be restored in a network in a hard fork kind of very straightforward way. Just turn them back on and fix the bugs. [Inaudible 00:30:45] they can be restored too, but it’s a little trickier. But justifying this in the bitcoin network is hard.
You know, I am very excited about fancy smart contracts in bitcoin more than most people I know and there was a time when myself and Peter Todd were like ninety per cent in the smart contract funkiness in the bitcoin network. But it’s hard to justify something it has had people risk when no one is using it. And of course no one’s using it because it’s not there. So there is like Catch 22.
There is also been in the deep recesses of the technical community a lot of very powerful ideas for new scripting systems which do things like, make the scripts very easy to start penalize to make sure that the script does what you think it would do. An important aspect of contract. And there’s a bunch of neat ideas that make things more efficient and so on, and maybe you know, it would be better the way until those were ready. But the whole idea with this elements project was to make experimentation cheap.
So if experimentation is cheap, why not go fix this stuff in script. And so that’s what Patrick did. This set of feature is basically re-enables all of the disabled op codes [inaudible 00:31:51] then operations. It adds few more fun things like the – like here’s a deterministic random number generator in the script and [inaudible 00:32:02] operation to check the signatures of arbitrary data passing on the staff which is actually a very powerful feature because you can use that to build balance for good behavior where you can say someone can make a probable stick payments and if they double spend it people can go collect their bond. You can do that using this – signature tracking for arbitrary data.
There’s many things you can do. One of the ones I like is, you can build one of a thousand multi signatures where the signatures only take about a hundred bytes in the transactions by building a Merkle tree it’s validated by the script update. And if you can do this and you can do things like put [inaudible 00:32:42] bitcoin all of your severs, put the different [inaudible 00:32:44] on every server. And when a server gets compromised and the attacker takes the bitcoin, you know which server is compromised because you just can see which of the one in a thousand multisig signed off.
Does this enable covenants? No, it does not currently enable covenants in deed. Next step, right? We also replaced the ECDSA signature with Schnorr. Schnorr is a different mathematical formulation for discrete log signatures. We’re using the same [inaudible 00:33:12] as bitcoin, but the Schnorr allows for a couple of improvements. One is highly efficient but non-accountable multi sig and back validation which gives us roughly 2x speed up which is nice. It also – the security proof for Schnorr are much more confidence boosting.
So speaking of signatures, there is another thing we’ve done in elements to improve signatures. So in bitcoin the only way that a – something like a hardware wallet knows the value of the coin it’s signing for is if you send to the hardware wallet that transaction that created the coin at spending. And the reason for this is because the only way that the value is committed to in a transaction is via the TXID of the coin being spent and this is the problem because your hardware device [inaudible 00:34:00] impose a policy like, actually telling you how much of the transaction is going to go to fees or to control how much you’re spending.
So if you have to screen the inputs to the hardware wallet you can create contrive cases where a transaction may need to have a gigabyte of data sent in to the hardware wallet before invalidate what the value is bitcoins that it’s spending which is ridiculous. There is a very simple and straightforward fix that’s quite easy to do and in a totally new network which is that you make the signature in the transaction directly cover the value rather than only cover it indirectly through the hash of the prior transaction. So this work that [inaudible 00:34:39] did and that’s all we did to make the signatures cover the values.
So next element in elements is a feature that is not something that would ever exist in the bitcoin network itself. And I think this highlights one of the interesting ways to use this mechanism of the two-way peg and building other networks is that you can experiment with ideas that are universally agreed upon as not very bitcoin.
So in bitcoin, we have the decentralized consensus hopefully, and it is essential for upholding bitcoins primary value. Albeit it is a trustless system. You get rid of the trustlessness and you’ve got like PayPal, but inefficiently implemented. So there’s no debate or any confusion here. But decentralized model of bitcoin is essential.
But what if you want to use the technology of bitcoin to build a private system or a semiprivate system? What if you want to build a low-value experimental system, small system? What is a decentralized system four people [inaudible 00:35:37]? What is that?
That’s not decentralized, it’s four people. And the mechanism with bitcoin uses for decentralized consensus is very fuzzy. It’s mining mechanism. It’s not secure when it’s used in small scale. So even if you are going to build something decentralized, how do you bootstrap it. Many altcoins have struggled with this bootstrapping problem and done a variety of things. So there are many other consensus models you can build systems out of, that exist in the wider world.
In Sidechains whitepaper, we get a framework for thinking about the bitcoin consensus model by describing it as a dynamic-membership multiparty-signature. This is the network is doing a threshold signatures where, you know, kind of, an N of M must sign off on the blocks. But who are the N of M? Well, it’s a dynamic membership chosen by their own participation in that file.
So what if you replace the dynamic-membership multiparty-signature with a multiparty-signature, plain multiparty-signature. Well, the result is a centralized security model. Although one which is arbitrarily better than just trust one server. Because you can build a system which is real-time audited by all of its participants, where most aspects of its behavior are [inaudible 00:36:45]. So you can say are the signers behaving or they not. I say most because, for example, we can’t tell if there are censoring in a very clean machine decidable way.
Now we could build the system it has arbitrary asterisk asterisk multisig policy. So you can say something like lots can be produced in this network if an auditor and five of these eight parties or eight of these eight parties allow it. And the asterisk asterisk is this is referring to the trust property of the system. In order to decide if you want to sign a block or not, you need to first have a consensus.
So if you had a policy, for example, it was like A and B or B and – A and B or C and D, right, a pair or another pair then that group could fork the network into two states because they were momentarily partitioned. And so not all policies make really good federated consensuses. So with this model, there’s no human discretion required, you could potentially implement the signers in the federated consensus on very robust tamper-resistant, tamper-detecting and self-destructing hardware. Some interesting opportunities there.
As I said, this isn’t a replacement for decentralized consensus. This is an extra tool, you can use in places where decentralized consensus is not the best. And there are some applications where you need to have trust in any case. If you’re building a system where all it does is trade around with gold notes and someone has to eventually redeem the digital gold notes for bars of gold. Well, then you have to trust that issuer to do that. So maybe you can use that issuer as part of a federated consensus. Why not use it, right, if that trust is there?
So this has been mostly the work of [inaudible 00:38:30]. And it’s something we’re using in elements and it allows us to have these elements network be rather secure even though right now it only has eight users. Hopefully more than eight by the end of the evening.
So the next and probably the most technically sophisticated feature of the set that I’m going to talk about tonight is the feature that we’re calling confidential transactions. So I thought before about the importance of privacy in the bitcoin sphere and I won’t belabor it forever. I think that that it’s very important to have privacy and systems of value transfer. The traditional money systems have privacy, right? When you make a bank transaction with someone, you know about the transaction, your receiver knows about the transaction, the bank knows about the transaction but the whole world doesn’t know about the transaction unless the bank has very poor security [inaudible 00:39:24].
So this is something like really table-state stuff and it’s kind of funny in the bitcoin space we’re so eager for bitcoin to be successful. Sometimes we wax over what a big limitation this is. Without adequate privacy, fraudsters can look at your financial records and target you. They can know exactly how to trick you. Thieves can go after the highest value targets, right? So you can go make a purchase and somebody says, “Hey, this guy’s got a bunch of money. I’m going to rob him, right?” This has incredible importance for businesses, because their negotiating positions depend on what you can spend. Like your margins or something that could be revealed if you were using bitcoin exclusively.
It’s also important for fungibility, especially when you talk about things like federated consensus systems which are not as decentralized. If you don’t have enough privacy, then it’s very easy for the participants in the network, even in the bitcoin network today that sends through your transactions and certainly in a system that is less decentralized than bitcoin and if coins are being selectively censored, you lose fungibility which is an important criteria for money.
So when talking about this, people go, but wait, but wait, bitcoins always got to be like this. It can’t be private because bitcoin is replacing the role of the bank. Bank can see your transactions. That’s how the bank keeps its record straight. And since bitcoin is the role of the bank and it’s a public decentralized network, the whole public has to see your transactions so it can keep your record straight. This isn’t true. It is completely possible to have total privacy and be completely compatible for public verification. And the easiest example for this is built right into every bitcoin transaction.
Consider digital signature. With your digital signature, you prove you know the private key. But you don’t tell everyone else your private key. That would sort of moot the point. So it can be done we just need the right technology. So bitcoin uses anonymity as its main mechanism for transaction privacy. But it’s turned out that certain limited thing in bitcoin has been really fragile and it works. But it doesn’t protect a lot of the cases that are important. When you transact with someone because of your transaction they usually know who you are. You go and buy a coffee. Well, in bitcoin, it’s very likely the person you just bought the coffee from can now see a substantial amount of your network information because of this transaction.
So [inaudible 00:41:41] looks all over the place and users reuse addresses often and it’s very weak. This lack of privacy in bitcoin isn’t just a thing that bothers [inaudible 00:41:53] guys in front of the room. This is something that comes up in every large institution that I’ve talked to about using bitcoin and bitcoin technologies. This lack of privacy is a major concern. And, of course, I care deeply about transparency. People look at the public ledger as a way to achieve great transparency. But data isn’t wisdom, right? You [inaudible 00:42:15] your information in a public blockchain might tell you something or maybe it’s really misleading.
True transparency requires a commitment to explain things and helping people understand them. So I don’t think that we lose out on transparency by having better privacy. And then, of course, there is concerns about harmful uses. But it turns out that harmful uses happen already in a system we have that is very not private. You know, where is the guy that stole Mt. Gox coins, right? Like, he’s not in jail.
AUDIENCE: In Japan.
So the harmful uses still happen even in a system that is conspicuously not private. And it turns out the people who are doing harmful things can afford to get privacy one way or another. They don’t need the system to help them. But more than anything else when I think about the subject, I think the experience we’ve had of the internet in general. I participate in the ITF and the work of many whose spirits are much greater than mine. And there’s this very widespread view now that we messed up.
We the community of people building the protocols of the internet messed up by not making encryption always on, can’t turn it off everywhere. And this discussion has come up in the ITF to apply crypto in more places many times throughout the years. There’s always been a reason to back off on it and make it optional or whatever, put in the corner, right? It’s complex, it’s slow, it’s incompatible. And all the reasons were true, right?
All of these things are true. It’s slow. It’s losing compatible. It’s complex. But when we think about it historically, these are one-time cost or small ongoing cost. And we should have [inaudible 00:43:52] way back then. And the longer we go without fixing them, the harder they are to fix. The more dependence there is. You know, the whole industry is right now the bill deep packet inspection devices, insert advertising and it’s your content on the internet, right? It is what it is. I’m not making moral judgment here. But they were able to exist because the internet did not have strong encryption.
If the internet had strong encryption way back when they wouldn’t exist. Right now, they paid lots of people to go to standards bodies and to fight against crypto on the internet. This isn’t the place we should be. This is a mess. So I think about this and I say, “Well, if bitcoin were really, you know, fantastic future to have displaced other systems of money in the world, but I don’t want to live in that world? And now how must we improve the privacy [story 00:44:34]. So what can we do?
I’m not the only person concerned about this. And there have been many people working on privacy in the bitcoin space. Many of the proposals, some of the [inaudible 00:44:43] . I group them into two sets: compatible and cryptographic. So compatible solutions were things you can do in the existing bitcoin network today without modification. Coinjoin, CoinSwap, centralized privacy servers. The compatible solutions are nice because they are immediately usable, but the privacy they provide is often very fragile usually due to people being able to trace the amounts. If you know X bitcoin come in and then exactly X coming out. Well, then it’s a pretty good guess that it was just the same user on both sides.
The cryptographic solutions generally have a different set of problems. So this would include things like Zerocoin. There is a proposal of Bitcoin Talk which people have never seen called one way aggregate signatures, another cryptographic privacy technique. There’s a traceable ring signature approach used by Bytecoin and Monero, Zerocash and the cryptographic solutions universally have this problem where they break [inaudible 00:45:40]. So in bitcoin to validate a new block on the network, you don’t need to know the whole history. You just need to know a small summary of the history and you can forget the rest of the history to validate a new block. This is critical for having good scalability in bitcoin, because you don’t want to have to do a random look up to the whole history to validate something.
The cryptographic solutions for privacy hide which coins have been spent and in doing so they break pruning completely. They also often need new cryptographic assumptions although that’s not true for the traceable ring signatures. They often have very poor performance. It’s just not implemented. Very completed and people haven’t done it yet or they’re keeping the private [inaudible 00:46:20] altcoin out of [inaudible 00:46:22] for whatever, right.
So let’s take a step back here. Prior work on cryptographic privacy has focused on the transaction graph, making the transaction graph private. And this is actually a little odd when you think about bitcoin transaction privacy from a frame work we used to think about internet protocol privacy. Because the transaction graph is really the metadata about the transaction whereas the content of the transaction is the destination, the value. Now, it’s very important to keep your metadata as private as you can. Keeping metadata private is often a losing battle. It’s very hard to do. It’s very expensive to do. So generally your internet except for thinks like [inaudible 00:47:01] or metadata is not made private, but the content is made private.
Well, what if you do just make the amounts of the transaction private? The destination of a transaction can be made private when using – by using the pseudonymous address or techniques like stealth address. All of the transaction amount are made private. And I think if you think about this it actually is the case that the amount is what needs to be private more often than the transaction history. And also if the amounts are private, all of these other schemes in the compatible [inaudible 00:47:33] things like CoinJoin are tremendously more powerful because their weakness comes from tracing the amounts. So if the amounts are private and they can be trace, CoinJoin are all perfect.
So the approach that we’ve taken for this, recalling confidential transactions is it replace the values, bitcoin amounts in transaction is 33 byte commitment which you can think of like a cryptographic hash, key cryptographic hash, but the commitment scheme we’re using preserves addition, meaning that you can take a set of commitments and add them up and you get the commitment to some of their values.
And with that property the network can still verify that the amounts of the transactions add up, that you haven’t created a coin out of nowhere. So this was originally proposed by Adam Back, my co-founder in 2013 in the BitcoinTalk thread called Bitcoins of hemolytic value. His original proposal was a little bit technically dense and it took a bit of work to make it sufficiently efficient. Mostly because there was one problem.
When you take a set of coins and we split them to create multiple outputs, the system can easily verify that the sum of the inputs is equal to the sum of the outputs. 1 plus 2 is equal to 1 plus 2, right. That the thing it can easily verify, but unfortunately 1 plus 2 plus is equal to negative 10 plus 13. If you have a negative value it still adds up. And so the system has to make sure you can’t make transaction that output negative amount of coin or you can create coins out of nowhere.
And so what you need is something called zero-knowledge range proof and the zero-knowledge rang proofs that we have are linear in the size of the value is that your expression. So in order to make this stuff efficient I invented a generalization of ring signatures which I published about last week as Brownian ring signature paper. And I used that as a building block to build the very efficient ring proof system and I believe there are many ring proof systems in literature, but I believe mine is the most efficient one yet described.
And what this allows you to do is to prove that a value is within a particular range using about 2.5 kilobytes for a value just 32 bits in size and I made this key inflexible so you can choose how much of the value you’re keeping private. But this is still a fair amount of data to a transaction. So the next thing that comes into this is the segregated witness part of the system. What segregated witness is these range proofs don’t have to be part of the data that you’re validating forever historically and then I came up with a cryptographic trick that allows you to – without adding anymore size, it allows you to reuse that – it allows you to reuse about 2 kilobytes of that 2.5 kilobytes to communicate a private message from the sender to the recipient. The people also often want to put messages like refund addresses, re-voice numbers, delivery addresses inside bitcoin transactions and it’s a little hard to stomach that on public network which is adding cost to everyone. But it can be accomplished as a drug side effect of the range proofs. Just looked in how do you [inaudible 00:50:52]. I suspect it can be improved. I did work quite a bit on it.
So I also have a technical write up that I’ll publish tonight that talks about all the techniques that I used. Like, then the proofs are actually decimal falling point numbers so they have an exponent separated on private. They are encoded in a mixture of base four and base two because reasons [inaudible 00:51:25]. And I’ll build on top the ring signature schemes through efficient [inaudible 00:51:30]. I think it can be improved further and I intend to work on improving it as it becomes possible to do so. So this whole scheme is compatible with transparency. You can use it to have watching wallets. There is a basically a watching key associated with a wallet, you can share. If somebody who has watching key, they can see all of your values without being able to spend your coins.
You can also share the blinding keys used for individual transactions. So you can prove to someone a payment had a specific value without revealing anything else. So this has been the project that I’ve mostly been dealing with. I had a lot of help from a lot of other people. So some future direction stuff.
All the stuff that I’ve talked about tonight is highly experimental and it’s at varying degrees of maturity, but definitely experimental. So I’m looking forward to seeing what interesting informative ways it will blow up and catch fire. I know the testnet itself has been getting some interesting attacks lately as well.
So I and the other folks that have worked on this plan to continue to refine these proposals and work on other ones. Some of them were suitable for using a bitcoin core. If they all mature then hopefully get them out there with the experience of actually running them in a network. As far as the whole elements project in general, there is a question. Will having the Sidechains mechanism in this test bed to do thing will result in the community that it builds new technology? Well, the fact that we can work on the system without rebooting the network effect, without seeking permission from anyone, right. You’re on Sidechain, right, you don’t have to ask me to do it. Without results and more development in this space, I’m not sure, but I look forward to finding out. Thank you.
Q&A
So, the two questions are these different features separate Sidechains? You know, they’re not. You’ve dumped them all into one and there will be many reasons to make them separate, that would be nice particularly when they fail it’d be easily to figure out exactly why they fail. But the problem is in running any network we know from the work we’ve done on bitcoin is that it’s just a tremendous amount of work in monitoring it and maintaining it, running nodes for it. And so it was easier for us to just put them all on the one system. Maybe this was a mistake because we’ve suffered a lot from the integration work actually that a lot of these changes conflicted with each other in good days.
The second question was related to the confidential transactions and basically, is it compatible with having the publicly verifiable transparent ledgers. It absolutely is. For one, you can just not use it, but the other way is that you could publish to whomever you want your watching keys for the wallets. And so, and you can publish into the world or you can publish them just to, you know, others, right. You can control it.
Q. [inaudible 00:54:26]?
A. Yes. So can people see the code? Yes, so where can we get it. Can you click in the blockstream website to get to it?
Q. Yes.
A. By the time you get to a computer you will be able to go to the blockchain website. It will lead you to a Github page which will link you to the elements project at Github page which has the code for all of it. You can download it and use it.
Q. So I can start [inaudible 00:55:06]?
A. Yeah, yeah.
Q. Projectelements.org doesn’t work.
A. Oh, projectelements.org doesn’t work, great. It works now.
Q. No. elementsproject.org.
A. Oh, elementsproject.org, is that correct?
Q. Yes.
A. Thank you.
Q. So I didn’t get clear answer last night, so when you transfer some bitcoins to the Sidechains [inaudible 00:55:27].
A. Yes. So the question here is, how do you do this, how does the bitcoin network know the rules in order to allow them blocking it?
Q. Right.
A. Right. So today the bitcoin network doesn’t and the testnet network doesn’t. They don’t know the rules [inaudible 00:55:48]. So the way we were accomplishing this for the elements alpha Sidechain is with this mechanism described in Appendix A of the Sidechains whitepaper called the Federated Peg. So there’s experimental work was that they are these trusted centralized parties that signed off on. It’s a trade off, but allows me [inaudible 00:56:07]. That’s why I can, you know, tell you something you can go and download and use today rather than some [inaudible 00:56:13] that you know, may get implemented five years from now.
Female: Can you guys wait for the mike please so everybody can hear your question? Thanks.
Q. Hi, Greg. I was just wondering has there been any progress made on atomic swaps [inaudible 00:56:32]?
A. So the limitation that the atomic swaps suffer is that the atomic swaps could secure these refund transactions and refund transactions are vulnerable to malleability. So there is another way to do an atomic swap without a refund transaction and that’s using the absolute checklock bond verifier. So I think, absolute checklock bond verifier is making nice progress is a good proposal. I think it’s on tract for deployment this year. It had to wait for another proposal to get locked on to the network. So I think once those are out there, we may see more activity on atomic swaps, but it’s hard to say, because you could do them today with just reduced security. People aren’t. Of course, they could be done on elements network immediately if you wanted to experiment there [inaudible 00:57:22] as well. So maybe some people that are holding off developing atomic swaps [inaudible 00:57:26] because they can’t do it securely on bitcoin might be more inclined to play within on elements where there’s checklock [inaudible 00:57:30] but I’m not sure.
Q. Hi, Greg. [Inaudible 00:57:35].
A. It is complicated. My system is a testnet fork. [inaudible 00:57:46] a little less complicated. Talk to your attorney.
Q. When it comes to [inaudible 00:57:58]. When it comes to the two-way peg and return coins from Sidechain back to bitcoin with let’s say via [inaudible 00:58:05] SPV proof verified. My understanding that the SPV wallet has [inaudible 00:58:14] that returns sidecoins back to bitcoin [inaudible 00:58:24] the entire Sidechain block.
A. So one of the appendix is I think it will be in the Sidechain’s whitepaper is a scheme for compact SPV proofs that basically allow you to show that a particular blockchain has a certain amount of work in it without revealing all of the evidence. It has more rhythmic scaling. So that’s something you don’t have to implement it today. So we have a stripped off code that does the proof verified which is used in the direction of testnet into the side chain. But it’s not used in the compact SPV proofs yet. We just haven’t implemented it. There is a bunch of free parameters in the design that we’ve been debating over for a long time. But there’s a scheme to make it very efficient and [inaudible 00:59:03].
Q. [inaudible 00:59:07] ask about your concerns around privacy. I was a little skeptical some of the arguments. Firstly, numerously people have [inaudible 00:59:17] will have lots of difference keypads and so we’ll use a set of key pay for small transactions and keep another keypad to [inaudible 00:59:30]. So I don’t really necessarily see the concern around me buying a coffee and therefore the coffee shops know exactly what my [inaudible 00:59:37]. A number of the other arguments [inaudible 00:59:42]. So we have lots of information about [inaudible 00:59:51] nice cars, nice hours. I don’t necessarily why [inaudible 01:00:00] we can see [inaudible 01:00:05]. Again your argument around [inaudible 01:00:11] negotiations. I don’t really see that, if someone has a budget, I don’t necessarily have to pay that whole budget to buy specific product or service. Why is that necessary a concern with negotiations?
A. None of these things make pure line rules, right. It’s not like if someone can see all your finances you can no longer negotiate, but every trade we make as one continues them, and there is a cost associated with it. So there will be some difference in the amount you pay when your opponent has more information and people don’t have to have that promiscuous transparency. They can just go use alternatives to bitcoin. And so if you can save money by using other systems then why not use it. It’s a disadvantage. Even if it’s so small. So I don’t necessarily feel a need to debate the details although I think it’s a bigger [inaudible 01:00:59]. Like this notion of people having separate addresses. In this room, maybe quite a few people have separate addresses. In the bitcoin space in general, people aren’t keeping their finances separate. It’s very difficult to do that. And even when you’re a very technically sophisticated user and I think I qualify as one, I’ve made many transaction that reveal a bunch of information about my finances accidentally, because it’s easy to mess up. And people can make a reasonable assured inferences about, you know, which coins we spent together or which addresses were used there. And there are things like data leaks where there is a tremendous amount to my personal financial information made public by someone else’s information being leaked out. And so these are all things that are made better by having better transparency in the system or better privacy in the system even if it’s not perfect.
Q. For the hiding of the amount stuff. That’s still leaks metadata information about what the inputs were and the outputs were.
A. Yeah, because you would – so that the – you learn a little bit about the values in two ways. One, the range proves themselves, prove that it’s in a range and you can make the proof smaller by making the range smaller. The – otherwise because obviously if there were – if there are plain text value somewhere in my history, you know, if there is only one bitcoin that went into this raft of transactions then my output can only ever be as much as one bitcoin, right. So there is still some information there. The key thing to keep in mind though is that if these confidential value transactions are used with CoinJoins then the sets of the coins coming out of the CoinJoin have the range – plausible range could basically be any of the sum of all the requests. So it can get pretty anonymous pretty quickly.
Q. I have a quick question. With the watching keys, are they revocable and can you tell who has them?
A. No, not today. That’s an interesting question. When I said there are areas to improve, one of the things that Adam and I’ve been working on for some time is in the context of stealth addresses. One of the problems with stealth addresses is this is a scheme for basically getting a one-time use address every time you transact but having a static address to give people. One of the problems with stealth address is you can ask other parties to scan for you, you can give blockchain.info your stealth address private key and they can scan for your transactions which is convenience, but they can always keep scanning for your transactions and then give away that key to other people. So for stealth addresses, Adam and I had come up with some schemes that use some fancier crypto that allow you to delegate for just finite ranges of blocks and those same schemes could be applied for watching wallets as well in this confidential value scheme. So potentially, you could make a watching wallet that was good only for a certain range of blocks. And maybe that moves more in the direction of having control over that, but it’s an open area to explore and until you asked about it I haven’t thought about it on this particular use.
Q. [inaudible 01:04:04] came through and they talk about having [inaudible 01:04:07] mechanism like that, but [inaudible 01:04:12].
A. Yeah, there’s things that can be done here. [inaudible 01:04:17] experiment. This isn’t a finished proposal, right. No one is saying go and put confidential value stuff in bitcoin today. This is a very raw and new system that needs to be analyzed and understood and optimized.
Q. Greg, have you thought about how to communicate for a given address what change that might be relevant algorithms?
A. Yeah. Right now we’re not doing anything really smart with that. There is a scheme that we come up with to allow registration, addresses and multiple chains, you could basically have an address sign off on, I am willing to accept coins in all of these different chains and then if you understand those chains you could pay to those addresses. One of the nice thing about it is this can be done with standard bitcoin address. So I give you a bitcoin address and if you’re also Sidechain aware you could automatically pay on the Sidechain sharing [inaudible 01:05:12], but that’s not implemented in this right now.
Q. So when the question regarding the two-way peg [inaudible 01:05:25] do I understand correctly that the main solution would be [inaudible 01:05:35] mining and if yes, what percentage do you anticipate would be needed on a Sidechain network?
A. So I think that the real challenge in that question is how do you [inaudible 01:05:54]. And nothing about the Sidechains proposal demands worth mining. It’s an option. Although not merge mining, you know, the question is would you merge miner, the question is would merge mining mean more security? We know for Namecoin that when Namecoins whole subsidy referred in real dollar value was half of what transaction fees are today in average on bitcoin. Namecoin achieve something like 80% of the bitcoin hash rate. So I think that’s evidence to suggest that if the soft recoil system around merge mining were done particularly well that very hash rate could be achieved. Is merge mining acceptably secure? That’s an extra more complicated question, it deals with incentives. And it’s a very hard question to answer because before you can answer that you have to answer the question, is bitcoin secure? And particularly is bitcoin secure not today but in a long run, because right now bitcoin securities is popped up by the distribution and subsidy. The subsidy is going away overtime and what bitcoin looks like in the future where subsidy is not providing the security, this environment closer to it can get right away with a merged mine Sidechain so that’s still an open question sort of filling out [inaudible 01:07:10].
Q. Next question. It’ll be on that last same question. Have you given any thought to having inflation on the return to bitcoin like if the elements Sidechains every block is a hundred bitcoins forever?
A. Yeah. It could be done, right. So notice the name of the two-way peg feature in elements is deterministic peg and what that’s really referring to the fact that the mechanism that controls the value ratio between Testnet and Alpha-Sidechain has really many deterministic function. We think the networks can compute. So you could imagine creating Sidechain that like had inflation in the Sidechain. It’s just that the coins in it would be increasingly backed by less and less bitcoin. So if you move coins back they get less bitcoin behind them. I’m – so some of my co-founders create an alt coin called Freicoin, which is an inflationary cryptocurrency. Has a bunch of interesting ideas behind it and nobody uses it, because they’re not really enamored by this inflationary aspect, but maybe it’s really ultimately a better design and I don’t have a – few of the fact that maybe there is a system which is in some economic sense superior, but no one wants to use it and they can choose not to use it so they won’t. And it’s like – I think that will also be the case for things like Sidechains that are created that have like inflationary ratios that people will choose not to use them because by writing up coins and chains it gets less valuable, but who knows.
Q. Even if it was that deflationary that every block then made in points is deleted [inaudible 01:08:53]
A. Yes.
Q. The return –
A. I want to see that. Well, I mean I have to say like ah, maybe the one we already created.
Q. Or do you test that?
A. Yeah, it’s tested.
Q. [inaudible 01:09:15] you were talking to create a [inaudible 01:09:16] and saying this is what the blockchain [inaudible 01:09:21]. Can you shed in [inaudible 01:09:23]?
A. So talking to people that want to looks at there’s basically in two areas that I have seen this in. I have seen this with people talking about tracking other kinds of assets and like equities and things like that and bitcoin like networks and there are all kind of complexities in doing that. And they did valid or not, but in any case one of the concerns that comes up is it’s the commercial confidentiality and that stuff. And in general, when just talking about it in terms as a remittance and payment system it come up as an issue. The conspicuous lack of privacy and you know, maybe the people I’m talking to we’re just mining for weaknesses, because there is a weakness in [inaudible 01:10:02], but I thought it was interesting that it isn’t really just that – in the bitcoin space the people would seek most about the sort of privacy area are the people would be super transgressive. You expect them to have [inaudible 01:10:15] down on the hand right. And really like I don’t think this is that political a thing. It’s a normal feature that financial systems have.
Q. Can you talk a little bit about what the future will be, what do you like to achieve in the next 6 months to 12 months on Sidechain elements?
A. Well, there is a couple of things I’d like to achieve. Some of the ideas that we’re working on is like [inaudible 01:10:42] stuff I’m sure are things that people would prop up with another try out are relatively straight forward and I’d like to just type on in the bitcoin, I guess. There are designs that people like and [inaudible 01:10:53] and I think that would be a success point to show that this actually can inculpate ideas for the random network. I’d like to also see use of this to try even further out ideas and that kind of stuff am talking about to you. And the area that we didn’t really explore [inaudible 01:11:14] is in improving fundamental technology improvement scalability of the system. There are many ideas that I feel [inaudible 01:11:21] about the last four or five years. There were the too [inaudible 01:11:26] without even trying it out. And so I like to see those tried out in the system, but more than anything else I like to see participation like – its an un answered question I have right now is why isn’t there more technical development in this space and there are many many ways that pulled back technical development. Cryptographic protocols are super hard and a number of people that knew about the stuff already is super small. Many of the people who are knowledgeable about this stuff think that bitcoin is a Ponzi scheme. Well, that’s getting better over time. And then there is the war of an alt coin. Like why would I go work on stuff on the bitcoin space or maybe I can do an alt coin make a bunch of money on that. This is attractive right, but I think that that’s petering out somewhat and it will be interesting to see how it evolves. So I want to see what the participation is like and will this be a tool to sort of jump-start a more couple of development on the underline infrastructure [inaudible 01:12:27].
Q. You already mentioned the problem in the future when the subsidy runs out so again future maybe in 25 years that the – if the total value of bitcoin is X whether it’s 1 billion or whatever, I don’t know. So the amount of money spent for mining should be only a small fraction of it.
A. Right.
Q. And then again the money that was needed to protect bitcoin would also be basically a scratch and that there is a problem I guess.
A. Right.
Q. Do you see a solution to this problem somewhere within the Sidechain project?
A. Well, I think that in the Sidechain project we may be in the ability to experiment with other ideas and that’s the most I can say in regard with this problem, but I think that’s actually one of the biggest challenges right now is experiment in a place we’re not off starting something totally new which had its own [inaudible 01:13:34] because it’s new. But there are many crypto alt coin I guess that fail not because their technology was bad, but because it never [inaudible 01:13:41]. You want to start a whole new thing like you’ve to sell both the currency and the technology. So I hope that it will help there. As far as that problem in general, well, one it would be a big problem to have to have this moon valued bitcoin in the future this where this is a real concern and I believe that if it is that case bitcoin is very valuable in the future so we should all be developed the moment we have the mechanism to go and develop, but I don’t have an answer to that and it’s one of the big unanswered questions [inaudible 01:14:12].
Q. Hi, Greg. I have a question around like what are the plans, you know, are there any [inaudible 01:14:19] to some change or is it the level be [inaudible 01:14:23]? The other question is like if someone will re-change [inaudible 01:14:28]?
A. Yeah, so one of the nice things about Sidechain is it’s a concept. It’s that they different and so things can – separate networks can coexist and transfer from [inaudible 01:14:42] body into the bitcoin testnet network. So there is nothing wrong with having more of them. I suspect that at least my vision on Sidechain all along has been it’s likely the case that there will be something like a power law distribution and networks in the future where there are some smaller numbers of networks that are very widely used that had the features that most people care about and then there will be lots and lots and lots of niche experimental things that are not [inaudible 01:15:06] many people, but I’m not sure, that’s just a guess. Let’s see what else is there in the question.
Q. Have you really change – improve Sidechain [inaudible 01:15:20]?
A. Yeah, if someone can start take the Sidechain elements off or start another chain with it like run another software, create another chain maybe [inaudible 01:15:26]. I’m not sure how that will pan out, depends on what the participation so I’m looking for a participation, but we’ll alert that what it exactly [inaudible 01:15:42]
Q. For the deterministic suit arrangement number in ratio.
A. Yes.
Q. What is [inaudible 01:15:47] and is it powerful enough to allow [inaudible 01:15:52] coin style proof of still having [inaudible 01:15:57]?
A. It could potentially be used for that, yeah, so what’s seeding it is input that comes on and off itself and so any date any way you can get dated of the transaction via other mechanisms for example.
Q. Like the [inaudible 01:16:10] that supply block number [inaudible 01:16:16]
A. Not currently. Well, sort of. What you can do right now is you could using the existing [inaudible 01:16:20] codes take a block header and validate it and used the hash of the block as the seed for the random number generator. That’s little update though. Hashes accepted. Yeah, what the random number generator is it’s basically just – it’s a opcode that takes a upper and a lower [inaudible 01:16:44] and efficiently runs to with the seed to produce a number in that balance and uniformly distribute it. And the seed is up to discreet.
Q. So first thing, it interesting to have a lot of thought into fixing the precede limitations in the side clause of the bitcoin technologies of that and there is very interesting possibilities here. My question is have you thought about other alt coins, you know, some of them were very different of course, but any thought given to compatibility with the Sidechain with other alt coins?
A. So depends on how you divide it up. I could, I think it would be not entirely fair to say, but I could say it’s immediately compatible but that’s what you are able to do with alt coins because the vast majority of it comes from bitcoin. And there is some alt coins where this is, this whole area design is compatible with and some where it’s not. I don’t know if that smart contract is done, but in terms of the other thing I talked about as well the – I mentioned that I need a generalized [inaudible 01:17:51] and I already pointed this out to the developers that in [inaudible 01:17:55] crypto currency it uses green signature in different way for privacy because if it had the scheme I cannot put [inaudible 01:18:02]. So I’m not really sure how [inaudible 01:18:08] and I have to say that because from just the first principle’s perspective I’m not too excited about alt coin approach to solving flexibility and crypto currency space. I don’t tract that maybe as well as, you know, [inaudible 01:18:26] I really want to be up to date with [inaudible 01:18:26]
Q. Okay. I have a question. [inaudible 01:18:28]
A. Yep, so in the case of block stream company our business is really focused on building fossils infrastructure and taking that technology and the bitcoin space to the wider world as well as improving it. Improving it for bitcoin itself. And building business even of them so doing things like block Sidechain for various applications, consulting work around some places. So there is a whole spectrum of business we’ll be doing half of this on infrastructure that could be built if the base infrastructure were good enough and so I think I’m going to share interest in improving that. We’ll see how it pans out.
Moderator: Next question. Come on guys [inaudible]. Perfect.
Q. If the Sidechain [inaudible 01:19:50] bitcoin core for whatever consensus is used like that would Elements ever operate on its own [inaudible 01:19:57] and actually a follow-up questions can elements operate as a parent [inaudible 01:20:02] its own Sidechain SPV verified [inaudible 01:20:05]?
A. It theoretically could. I’m not sure, certainly can be made to, right. It’s not done software so the answer is always yes. Sidechain can do it. I mean I don’t have any interest in creating an alt coin out of this for the reasons that I said before. Actually one of the jokes I was making before this, before releasing we should have an office [inaudible 01:20:27] how long till an alt cons like built out and stuff although I’m very afraid for anyone who does that. Because the software is not very mature at this point. So I think people will do this and it isn’t specific elements right. When we created that P2SH functionality in bitcoin it took us month to maturity and get it deployed. The first version [inaudible 01:20:49]. This took us a numbers of months to get to the level of maturity where we really could deploy it in bitcoin. During that time an alt coin arose that basically advertising this great new feature set which then, you know, copy description P2SH and it was announced with exchange integration on the first like hour of its creation. Which is what it is, it maybe a little disappointing that work on something cool and then have someone competing with you using your own code or I mean this is the case, so this is what it is in bitcoin. It’s one of the prices of free software. And I think that the flexibility that the software it does not have inherent, the fact that the software is free allows people to this, but it must be free if it is to give the users the freedom they need to trust it as a currency to [inaudible 01:21:36].
Moderator: Okay, and if that’s all we have I’ll wrap it up for today. Everybody, thank you so much for coming out and one round of applause to Greg Maxwell.
