What Is Zcash?
Since the dawn of Bitcoin way back 2008, Zcash is one of the latest player on block of cryptocurrencies. Through the years, many altcoins have came out also from any part of the world and that is from Bitcoin inspiration where Zcash is one of them.
A large portion of these renditions have attempted to concoct some upper hands opposite bitcoin, and keeping in mind that few have seen premium, many work with a little market capitalization, volumes and flow.
Enter Zcash, a decentralized and open-source digital currency, which looks encouraging. "In the event that Bitcoin resembles http for cash, Zcash is https," is the manner by which it characterizes itself. Zcash offers protection and specific straightforwardness of exchanges.
Along these lines like https, Zcash cases to give additional security or protection where all exchanges are recorded and distributed on a blockchain, however subtle elements, for example, the sender, beneficiary, and sum stay private.
Zooko Wilcox, Founder and CEO of Zcash, told Investopedia, "Zcash is another blockchain and cryptographic money which permits private exchanges (and by and large private information) in an open blockchain. This permits organizations, buyers, and new applications to control who gets the chance to see the points of interest of their exchanges, even while utilizing a worldwide, authorization less blockchain."
Zcash offers its clients the decision of 'protected' exchanges, which take into account substance to be encoded utilizing progressed cryptographic strategy or zero-learning evidence development called a zk-SNARK created by its group.
These developments guarantee legitimacy of exchanges and also secure record of parities without giving out some other data, (for example, gatherings or sum included). Consequently Zcash offers an additional element over bitcoin, while guaranteeing that no one is conning or taking.
Prior this year, the Zcash Electric Coin Company raised a sum of $2 million in return for value in the organization from seventeen financial specialists: Aaron Grieshaber, Branson Bollinger, Maple Ventures (Amir Chetrit and Steven Nerayoff), Brian Cartmell, Vlad Zamfir, Roger Ver, Digital Currency Group, Barry Silbert, Charles Songhurst, Fenbushi, Shapeshift, Erik Voorhees, David Lee Kuo Chuen, Fred Ehrsam, Sebastian Serrano, and Li Xiaolai.
Zcash has caused a considerable measure of debate for its technique for appropriating the digital money. The association isn't set up as an opensource group yet as a Company. This is the principal significant distinction to Bitcoin and other cryptographic forms of money, for example, ethereum.
The second significant distinction is the means by which they intend to compensate financial specialists and laborers in the Company which is by a duty on mining rewards called "Organizers remunerate".
The premine has been the worst thing about all cryptographic money fans - however the line has turned out to be obscured between what is correct and what isn't right. In any case, in the meantime the computerized money makers should be boosted to keep the venture running and they frequently do this by propelling a digital currency and issuing coins to different individuals which are then dumped available discouraging the cost - the engineer soon loses premium and the task is left sitting.
With Zcash they have adopted an alternate strategy and have taken cash from financial specialists in the organization to make the cryptographic money before discharging it. Be that as it may, here comes the catch - for each unit of Z money you mine amid the initial 4%, the Company that runs Zcash gets 20%, which will add up to 10% of the aggregate supply.
To a few people this has been causing concern and wrath as they feel that the financial specialists are utilizing the system to unreasonably enhance themselves by the power that they control. The benefactors incorporate Pantera Capital and different Bitcoin famous people, for example, Roger Ver and Barry Seibert.
In some ways however this approach is sensible as it adjusts the long haul objectives of the Zcash people group and the Company - i.e. to make it a win and give it the capacity to subsidize itself to keep up advancement and research. The flipside is they are not revealing who gets what from the mined coins - i.e. what amount goes towards the financial specialists and the amount to the workers and officers of the Company.
The other point is that Zcash is being pushed by one of its speculators - the Digital Currency Group, which possesses an expansive level of the media outlets engaged with the cryptographic money space inciting some to blame ZCash for being a result of corporate insatiability.
There has been a considerable measure of chat on discussions about this - and with the coin being open source, there have been some recommending they will make their own money in view of the very same conventions yet without the 10% duty on mining rewards.
Getting Started With Zcash
Zcash encrypts the contents of shielded transactions. Since the payment information is encrypted, the protocol uses a novel cryptographic method to verify their validity.
Zcash uses a zero-knowledge proof construction called a zk-SNARK, developed by our team of experienced cryptographers based on recent breakthroughs in cryptography. These constructions allow the network to maintain a secure ledger of balances without disclosing the parties or amounts involved.
Instead of publicly demonstrating spend-authority and transaction values, the transaction metadata is encrypted and zk-SNARKs are used to prove that nobody is cheating or stealing.
Zcash also enables users to send public payments which work similarly to Bitcoin. With the support for both shielded and transparent addresses, users can choose to send Zcash privately or publicly. Zcash payments sent from a shielded address to a transparent address reveal the received balance, while payments from a transparent address to a shielded address protect the receiving value.
Zcash is a private cryptocurrency that supports transparent and shielded transactions. Before using Zcash, review our privacy and security recommendations to learn more about its privacy enhancing properties and learn how to use shielded transactions correctly. Visit our technology page to learn more about the cryptography behind Zcash.
What are zk-SNARKs?
Zcash is the first widespread application of zk-SNARKs, a novel form of zero-knowledge cryptography. The strong privacy guarantee of Zcash is derived from the fact that shielded transactions in Zcash can be fully encrypted on the blockchain, yet still be verified as valid under the network’s consensus rules by using zk-SNARK proofs.
The acronym zk-SNARK stands for “Zero-Knowledge Succinct Non-Interactive Argument of Knowledge,” and refers to a proof construction where one can prove possession of certain information, e.g. a secret key, without revealing that information, and without any interaction between the prover and verifier.
“Zero-knowledge” proofs allow one party (the prover) to prove to another (the verifier) that a statement is true, without revealing any information beyond the validity of the statement itself. For example, given the hash of a random number, the prover could convince the verifier that there indeed exists a number with this hash value, without revealing what it is.
In a zero-knowledge "Proof of Knowledge" the prover can convince the verifier not only that the number exists, but that they in fact know such a number - again, without revealing any information about the number. The difference between "Proof" and "Argument" is quite technical and we don't get into it here.
“Succinct” zero-knowledge proofs can be verified within a few milliseconds, with a proof length of only a few hundred bytes even for statements about programs that are very large. In the first zero-knowledge protocols, the prover and verifier had to communicate back and forth for multiple rounds, but in “non-interactive” constructions, the proof consists of a single message sent from prover to verifier.
Currently, the only known way to produce zero-knowledge proofs that are non-interactive and short enough to publish to a block chain is to have an initial setup phase that generates a common reference string shared between prover and verifier. We refer to this common reference string as the public parameters of the system.
If someone had access to the secret randomness used to generate these parameters, they would be able to create false proofs that would look valid to the verifier. For Zcash, this would mean the malicious party could create counterfeit coins. To prevent this from ever happening, Zcash generated the public parameters through an elaborate, multi-party ceremony.
To learn more about our parameter generation ceremony and see the precautions we’ve taken to prevent the secret randomness essential to Zcash from being exposed (e.g. computers being blowtorched), visit our Paramgen page. To learn more about the math behind the parameter generation protocol, read our blog post or whitepaper on the topic.
HOW ZK-SNARKS ARE CONSTRUCTED IN ZCASH
In order to have zero-knowledge privacy in Zcash, the function determining the validity of a transaction according to the network’s consensus rules must return the answer of whether the transaction is valid or not, without revealing any of the information it performed the calculations on.
This is done by encoding some of the network's consensus rules in zk-SNARKs. At a high level, zk-SNARKs work by first turning what you want to prove into an equivalent form about knowing a solution to some algebraic equations.
In the following section, we give a brief overview of how the rules for determining a valid transaction get transformed into equations that can then be evaluated on a candidate solution without revealing any sensitive information to the parties verifying the equations.
Computation → Arithmetic Circuit → R1CS → QAP → zk-SNARK
The first step in turning our transaction validity function into a mathematical representation is to break down the logical steps into the smallest possible operations, creating an “arithmetic circuit”.
Similar to a boolean circuit where a program is compiled down to discrete, single steps like AND, OR, NOT, when a program is converted to an arithmetic circuit, it’s broken down into single steps consisting of the basic arithmetic operations of addition, subtraction, multiplication, and division (although in our particular case, we will avoid using division).
Here is an example of what an arithmetic circuit looks like for computing the expression (a+b)*(b*c) :
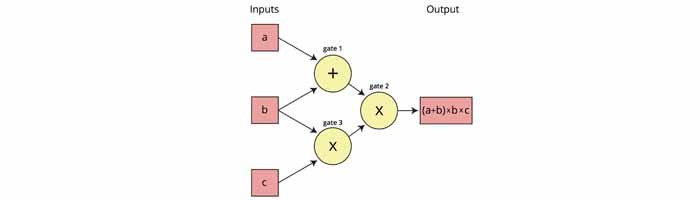
Looking at such a circuit, we can think of the input values a, b, c as "traveling" left-to-right on the wires towards the output wire. Our next step is to build what is called a Rank 1 Constraint System, or R1CS, to check that the values are “traveling correctly”. In this example, the R1CS will confirm, for instance, that the value coming out of the multiplication gate where b and c went in is b*c.
In this R1CS representation, the verifier has to check many constraints — one for almost every wire of the circuit. (For technical reasons, it turns out we only have a constraint for wires coming out of multiplication gates.) In a 2012 paper on the topic, Gennaro, Gentry, Parno and Raykova presented a nice way to “bundle all these constraints into one”. This method uses a representation of the circuit called a Quadratic Arithmetic Program (QAP).
The single constraint that needs to be checked is now between polynomials rather than between numbers. The polynomials can be quite large, but this is alright because when an identity does not hold between polynomials, it will fail to hold at most points. Therefore, you only have to check that the two polynomials match at one randomly chosen point in order to correctly verify the proof with high probability.
If the prover knew in advance which point the verifier would choose to check, they might be able to craft polynomials that are invalid, but still satisfy the identity at that point. With zk-SNARKs, sophisticated mathematical techniques such as homomorphic encryption and pairings of elliptic curves are used to evaluate polynomials “blindly” - i.e. without knowing which point is being evaluated.
The public parameters described above are used to determine which point will be checked, but in encrypted form so that neither the prover nor the verifier know what it is.
The description so far has mainly addressed how to get the S and N in “SNARKs” — how to get a short, non-interactive, single message proof — but hasn’t addressed the “zk” (zero-knowledge) part which allows the prover to maintain the confidentiality of their secret inputs. It turns out that at this stage, the “zk” part can be easily added by having the prover use “random shifts” of the original polynomials that still satisfy the required identity.
For a step-by-step, in-depth explanation of key concepts behind zk-SNARKs in Zcash, see our SNARKs Explainer series with posts on:
- Homomorphic Hiding
- Blind Evaluation of Polynomials
- The Knowledge of Coefficient Test and Assumption
- How to make Blind Evaluation of Polynomials Verifiable
- From Computations to Polynomials
- The Pinocchio Protocol
- Pairings of Elliptic Curves
Zcash uses a fork of libsnark, a C++ library for zk-SNARKs. You can inspect the code and learn more about our implementation on github. For a deeper dive into the protocol used for Zcash’s zk-SNARKs, refer to this paper on the Pinocchio protocol.
HOW ZK-SNARKS ARE APPLIED TO CREATE A SHIELDED TRANSACTION
In Bitcoin, transactions are validated by linking the sender address, receiver address, and input and output values on the public blockchain. Zcash uses zk-SNARKs to prove that the conditions for a valid transaction have been satisfied without revealing any crucial information about the addresses or values involved. The sender of a shielded transaction constructs a proof to show that, with high probability:
- the input values sum to the output values for each shielded transfer.
- the sender proves that they have the private spending keys of the input notes, giving them the authority to spend.
The private spending keys of the input notes are cryptographically linked to a signature over the whole transaction, in such a way that the transaction cannot be modified by a party who did not know these private keys.
In addition, shielded transactions must satisfy some other conditions that are described below.
Bitcoin tracks unspent transaction outputs (UTXOs) to determine what transactions are spendable. In Zcash, the shielded equivalent of a UTXO is called a “commitment”, and spending a commitment involves revealing a “nullifier”.
Zcash nodes keep lists of all the commitments that have been created, and all the nullifiers that have been revealed. Commitments and nullifiers are stored as hashes, to avoid disclosing any information about the commitments, or which nullifiers relate to which commitments.
For each new note created by a shielded payment, a commitment is published which consists of a hash of: the address to which the note was sent, the amount being sent, a number “rho” which is unique to this note (later used to derive the nullifier), and a random nonce.
Commitment = HASH(recipient address, amount, rho, r)
When a shielded transaction is spent, the sender uses their spending key to publish a nullifier which is the hash of the secret unique number ("rho") from an existing commitment that has not been spent, and provides a zero-knowledge proof demonstrating that they are authorized to spend it. This hash must not already be in the set of nullifiers tracking spent transactions kept by every node in the blockchain.
Nullifier = HASH(spending key, rho)
The zero-knowledge proof for a shielded transaction verifies that, in addition to the conditions listed above, the following assertions are also true:
For each input note, a revealed commitment exists.
The nullifiers and note commitments are computed correctly.
It is infeasible for the nullifier of an output note to collide with the nullifier of any other note.
In addition to the spending keys used to control addresses, Zcash uses a set of proving and verifying keys to create and check proofs. These keys are generated in the public parameter ceremony discussed above, and shared among all participants in the Zcash network.
For each shielded transaction, the sender uses their proving key to generate a proof that their inputs are valid. Miners check that the shielded transaction follows consensus rules by checking the prover’s computation with the verifying key.
The way that Zcash’s proof generation is designed requires the prover to do more work up-front, but it simplifies verifying, so that the major computational work is offloaded to the creator of the transaction (this is why creating a shielded Zcash transaction can take up to 40 seconds, while verifying that a transaction is valid only takes milliseconds).
The privacy of Zcash’s shielded transactions relies upon standard, tried-and-tested cryptography (hash functions and stream ciphers), but it's the addition of zk-SNARKs, applied with the system of commitments and nullifiers, that allows senders and receivers of shielded transactions to prove that encrypted transactions are valid.
Other methods of providing privacy for cryptocurrencies rely upon obscuring the linkage between transactions, but the fact that Zcash transactions can be stored on the blockchain fully encrypted opens up new possibilities for cryptocurrency applications. Encrypted transactions allow parties to enjoy the benefits of public blockchains, while still protecting their privacy.
Planned future upgrades will allow users to selectively disclose information about shielded transactions at their discretion. See our Near Future of Zcash blog post on future plans for Zcash.
For a more in-depth explanation of how shielded transactions are constructed in Zcash, see our blog post on How Transactions Between Shielded Addresses Work. For full details on the current Zcash protocol, refer to our protocol specification.
FUTURE APPLICATIONS OF ZK-SNARKS
Creating shielded transactions in Zcash is only one example out of many possible applications of zk-SNARKs. Theoretically, you can use a zk-SNARK to verify any relation without disclosing inputs or leaking information.
Generating proofs for complex functions is still too computationally intensive to be practical for many applications, but the Zcash team is pushing the boundaries for optimizing zk-SNARKs, and is already breaking new ground with more efficient implementations.
As it currently stands, Zcash's implementation of zk-SNARKs can be added to any existing distributed ledger solution as a Zero-knowledge Security Layer for enterprise use cases. The scientists on the Zcash team are among the most knowledgeable researchers of zk-SNARKs in the world, and are constantly working on coming up with new applications and improving the efficiency of zero-knowledge protocols.
If you have a business need that could benefit from the application of zero-knowledge proofs or blockchain solutions with robust privacy, get in touch with our business development team.
CHOOSING A WALLET
Before you acquire some Zcash, you'll want to make sure that you have a wallet set up to store it. You can download the official Zcash client or use a third-party application to manage your funds.
The official Zcash client is built for Linux, but community members have modified it for Windows and MacOSX. Visit our download page for installation instructions.
Find a third-party wallet that supports Zcash (many wallet providers currently only support transparent addresses, since they are easier to integrate).
GETTING ZCASH
If you just want to get some Zcash to use, you can buy online from an exchange. Find an exchange that supports Zcash.
To start mining Zcash, check out the mining guide on our wiki, or see this list of Zcash mining pools with instructions on how to get started.
If you're interested in accepting Zcash as a payment option, feel free to contact us for advice and integration support.
JOINING THE COMMUNITY
Zcash launched in the fall of 2016, and is still being integrated into applications and exchanges. To discuss topics like mining, use cases, and ongoing development, join our community chat or our forum.
How To Get A Zcash Wallet?
There are several types of wallets available for you to download to hold your Zcash.
Internet Wallets – Are the fastest way to start accepting Zcash. Many of the websites below also have an App you can download for your phone to manage your Zcash. Be sure to use strong passwords and enable factor authentication when it is available. CryptoCompare has a nice guide to help you research before choosing.
Web based applications/wallets that work with Zcash Transparent Addresses:

Hardware Wallets – Hardware wallets are the safest way to store your Zcash and other crypto-currencies. The main drawback (for now) is that they only support Zcash Transparent Addresses and they cost between $40-$99. You purchase a physical device which has a number of safeguards to prevent theft and have emergency steps you can take to recover your Zcash if your device is lost.

Local Wallets – These Wallets run the Zcash client and a full network node on your Computer. These are a little more technical to set-up and use. To use Zcashs Private Addresses you will need to download one of these:

Note: The first link above is for the Official Zcash Client, the Windows and Mac releases are maintained by David Mercier .You can find a list of the API commands to use with these Zcash wallets Here.
If you like to dig into code there are some very cool Zcash wallet projects that you can use and contribute to on Github:

Exchange Wallets – Exchange wallets are one of the easiest to set up because all you have to do is create an account with one of the many Exchanges that support Zcash. After you create an account it is very simple to generate an address to receive/spend or trade Zcash. No exchanges currently support Zcash Private Addresses.
IMPORTANT: The most important thing you need to keep in mind about wallets is that by using a wallet (whether on your own computer, on an app, or on an exchange) YOU are acting as your own Bank. If you lose, misplace, forget your password, or are somehow hacked then your Zcash will be lost forever. Be very careful when dealing with wallets and always use strong passwords to help protect yourself.
Here are a few videos explaining how to create and use the different types of wallets:
Zcash Resources
- FAQ
- Security
- Public Keys
- Media Kit
- Copyright Policy
- Trademark Policy
- Forum
- Community Dev Chat
- IRC:irc.oftc.net #zcash
How To Buy Zcash?
Mining isn't for everybody, however. It requires a specific level of learning and time. As thus, purchasing Zcash specifically from a trade is frequently the most effortless approach to obtain it. Be that as it may, enrolling on a trade will frequently expect you to uncover your own data, however once you have Zcash in your wallet, you can simply transform it into a private address.
In this guide, we will utilize the Kraken trade. Kraken is a legitimate trade and it is very simple to utilize. Besides, it's one of only a handful couple of spots where clients can purchase Zcash for fiat money (EUR, USD, and so forth).
So, let's get started!
Part 1 - Create an account
Step 1: Click here to visit Kraken
Step 2: Click "Sign Up"
Step 3: Enter your personal information, agree to the terms & conditions and click "Sign Up"
Step 4: Confirm your email address and log into your account
Part 2 - Verify your identity.
In order to be able to exchange cryptocurrencies for national currencies and vice versa, you'll need to verify your identity. This will allow you to buy and sell Zcash to your bank account.
Step 1: Click "Get Verified"
If you want to be able to deposit and trade cryptocurrencies, you can get Tier 1, but if you want to deposit/withdraw national currencies you must activate Tier 2
Step 2: Scroll down and fill your personal information and click "Get Verified"
Step 3: Once that's done, advance to the second tier by clicking "Get tier 2 verified"
Step 4: Do the same you did in Step 2, enter your information and click "Get Verified"
If you want to increase your limits, you can verify your account up to Tier 4
Part 3 - Deposit
Step 1: Scroll up and click "Funding"
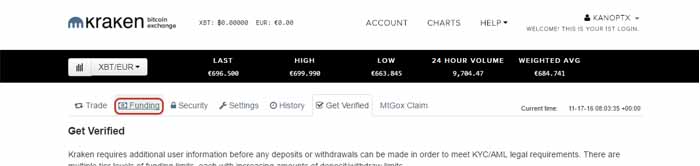
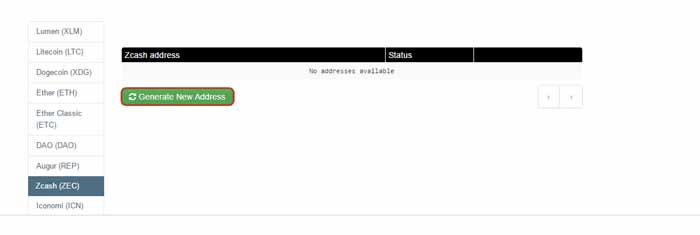
Step 2: If you want to deposit Zcash, scroll down and choose "Zcash (ZEC)" at the bottom

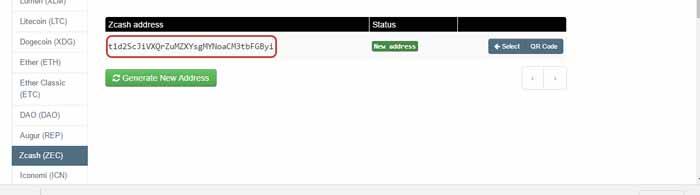
Step 3: Click "Generate New Address"
Step 4: Deposit Zcash to the address displayed
Step 5: If you want to deposit a national currency (We'll use EUR), choose one of the fiat currencies at the top
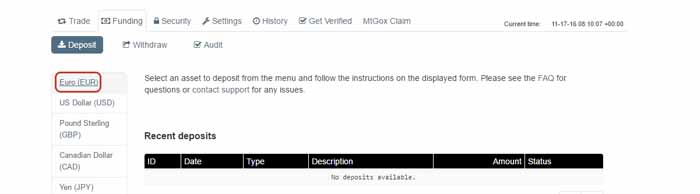
Step 6: Select the deposit method
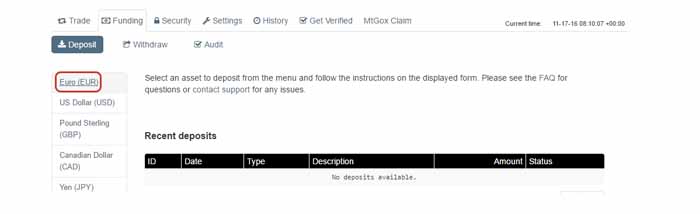
Step 7: Scroll down and follow the instructions shown
It may take some days to credit your national currency, especially if you've never deposited a national currency with Kraken. Once your fiat arrives, it's time to buy some Zcash.
Part 4 - Buy Zcash with USD/EUR
Now that your money has arrived, time to buy Zcash.
Step 1: Go to "Trade"
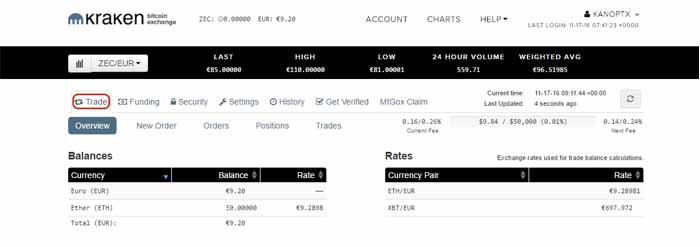
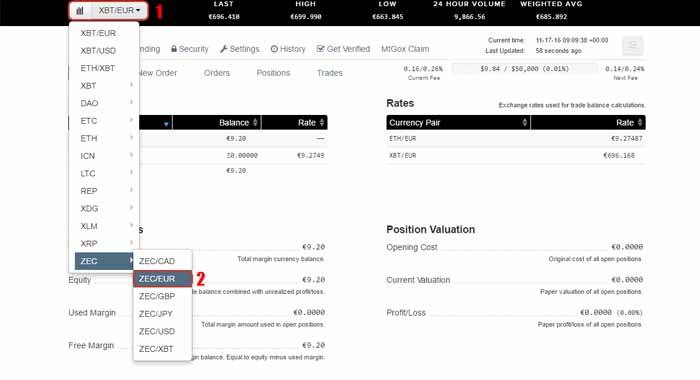
Step 2: Select your pair. Click the current pair (1) and choose the one you want (2). We are going to use ZEC/EUR
Step 3: Now click "New Order"
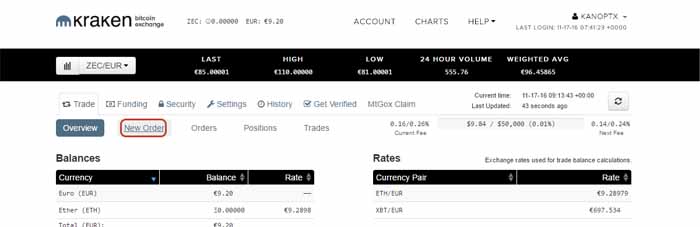
There are many types of orders, which Kraken has split into Simple, Intermediate and Advanced. For the purposes of this guide we'll only need to place a simple order.
Step 4: Now enter the price you want to pay and the amount of EUR you want to spend. The Zcash you're going to buy will be calculated automatically.
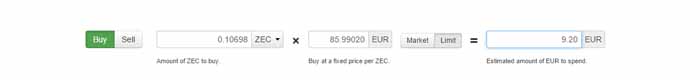
If you are not sure about which price to choose, you can always check the orderbook by clicking "Charts" on the top right corner
Step 5: Click "Buy ZEC with EUR"
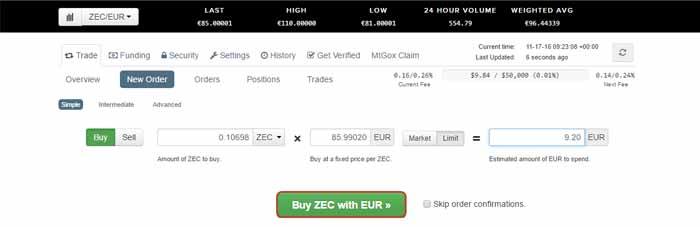
Step 6: Click "Submit Order" to confirm
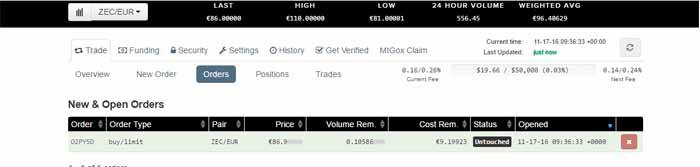
Step 7: Now wait for your order to be taken. The time it takes will depend on how good your price is
How To Earn Zcash?
Like Bitcoin, Zcash is a mined cryptocurrency, which means that new ZEC will be created each time a block is added to the Zcash block chain. New blocks will be created roughly every 150 seconds (2.5 minutes).
The monetary supply curve will mirror Bitcoin’s, except that, because Zcash’s blocks will be mined 4 times as frequently as Bitcoin’s, the number of ZEC created per Zcash block will be a quarter the number of BTC created per Bitcoin block. The first weeks after Zcash launch will be in a “slow-start” mining period.
Zcash enhances privacy for users by encrypting sender, amount and recipient data within single-signature transactions published to its public block chain ledger.
Zcash does not: encrypt data for multisignature, protect against correlations made with public transactions (for example, when Zcash is traded to/from another cryptocurrency) or obfuscate IP addresses. It is possible to use it in conjunction with an anonymizing network such as Tor, in order to obtain protection against network eavesdropping which is complementary to transaction privacy.
It should be noted that while Zcash facilitates anonymization for its users amongst a wide pool of individuals, we align more with the term “privacy” to describe what Zcash technology aims to provide. While related in scope, the terms have subtle differences.
Anonymity relates to removing personal identifiers linked to potentially public data such as sending an anonymous tip to law enforcement or wearing a mask during a protest.
Privacy considers the data itself in need of protection such as a discussion during a private meeting and more relevant, the encryption of information - whether for keeping personally or sharing with a select number of others. Anonymity methods can enhance privacy goals, such as defending against targeted attacks on private data, and vice versa if the protected data relates to personally identifiable information.
The encryption of data in private Zcash transactions aligns with the latter as it is foremost a tool for financial privacy with the added benefit of increased anonymity.
Where To Spend Zcash?
Zcash has also announced some additional details on its investors and previous fundraising structures.
Its latest funding round of $2m was raised for 6.25% of the company, implying a valuation of $32m, while its previous round of $1m was raised for 10.15% of the company, implying a valuation of about $10m.
Thus, the early investors paid about $1m for equity in the Zcash Electric Coin Company and 214,000 ZEC over the first year (about $4.66 per ZEC), while the most recent investors paid about $2m for equity and 132,000 ZEC (about $15.15 per ZEC).
Another important concept to keep in mind with Zcash is the thought of the technology also being applied to other projects or protocols.
There are even existing plans and talks around extending some of the functionality behind Zcash to ethereum, and possibly vice versa – bringing smart contract features to Zcash.
Thus, the value of ZEC will obviously be based a multitude of factors, and consideration should be given to comparable and even competitive platforms and assets like BTC, ETH and future projects that can also adopt and iterate on these groundbreaking and open-source developments.
What Is Zcash Mining?
Setup
First, you need to set up your local Zcash node. Follow the [1.0 User Guide](1.0 User Guide) up to the end of the section "Compiling", then come back here. (You can also do the "Testing" section if you want!)
Configuration
Configure your node as per 1.0-User-Guide#configuration, including the section Enabling CPU Mining.
Mining
Now, start Mining!
$ ./src/zcashd
To run it in the background (without the node metrics screen that is normally displayed):
$ ./src/zcashd -daemon
You should see the following output in the debug log (~/.zcash/debug.log):
Zcash Miner started
Congratulations! You are now mining on the mainnet.
To stop the Zcash daemon, enter the command:
$ ./src/zcash-cli stop
Spending Mining Rewards
Coins are mined into a t-addr (transparent address), but can only be spent to a z-addr (shielded address), and must be swept out of the t-addr in one transaction with no change. Refer to our 1.0 User Guide for instructions on how to use the z_sendmany command to send coins from a t-addr to a z-addr. You will need at least 4GB of RAM for this operation.
Mining pools
If you're mining by yourself or at home, you're most likely to succeed if you join an existing mining pool. See this community-maintained list of mining pools for further instructions.
P2PKH transactions
The internal zcashd miner inherited from Bitcoin used P2PK for coinbase transactions, but Zcash 1.0.6 and later use P2PKH by default, following the trend for Bitcoin.
Configuration options
Mine to a single address
The internal zcashd miner uses a new transparent address for each mined block. If you want to instead use the same address for every mined block, use the -mineraddress= option available in Zcash 1.0.6 and later.
Latest Zcash News
Ethereum Adoption of zk-SNARK Technology
The Ethereum Metropolis (Byzantium) upgrade adds a new cryptographic tool (zk-SNARKs) that was pioneered by Zcash. The addition of zk-SNARK technology into Ethereum is another validation, like the JP Morgan partnership, that privacy and auditability are important for business and for the economy, and that zk-SNARKs are the premier technology for privacy and auditability.
Cultivating Sapling: Faster zk-SNARKs
Zcash's next major upgrade, codenamed Sapling, will feature a set of groundbreaking performance improvements for our shielded transactions. In the last blog post of this series, we talked about a new elliptic curve for zk-SNARKs called BLS12-381, as well as new proving systems and other algorithms.
Celebrating the Zcash Developer Community
Since the launch of Zcash about 10 months ago, we've seen a promising selection of support from a variety of third-party developers. New and existing businesses have adopted Zcash into their wallet and exchange platforms which has helped to create a strong start for the ecosystem.
Cultivating Sapling: New Crypto Foundations
Zcash's next major protocol upgrade, codenamed Sapling, will feature a number of improvements to the performance, security and usability of our shielded transactions. This is the first in a series of blog posts that will explore progress made in Sapling's development.
