What Is Cardano?
Cardano is used to receive and send digital money and a home to the Ada cryptocurrency. This computerized money speaks to the fate of cash, influencing conceivable quick, to coordinate exchanges that are ensured to be secure using cryptography.
Cardano is something other than a digital money, be that as it may, it is an innovative stage that will be fit for running monetary applications as of now utilized each day by people, associations and governments all around the globe.
- Overview - Table of Contents
- What Is Cardano?
- Getting Started With Cardano
- How To Get A Cardano Wallet?
- Cardano Resources
- How To Buy Cardano?
- How To Earn Cardano?
- Where To Spend Cardano?
- What Is Cardano Mining?
- Latest Cardano News
The stage is being developed in layers. This gives the framework the adaptability to be all the more effectively kept up and consider updates by method for delicate forks. After the settlement layer that will run Ada is finished, a different registering layer will be worked to deal with smart contracts, the advanced legitimate understandings that will support future trade and business.
Cardano will likewise run decentralized applications, or dapps, administrations not controlled by any single gathering but rather work on a blockchain.
This is the first blockchain project to be developed from a scientific philosophy, and the only one to be designed and built by a global team of leading academics and engineers. It is essential that the technology is secure, flexible and scalable for use by many millions of users.
Consequently, considerable thought and care from some of the leading experts in their fields has been devoted to the project and informed design decisions. The scientific rigour applied to mission-critical systems such as aerospace and banking has been brought to the field of cryptocurrencies, with a high assurance implementation. We believe this is the first time that this has been done.
A major innovation of Cardano is that it will balance the needs of users with those of regulators, and in doing so combine privacy with regulation. The vision for Cardano is that its new style of regulated computing will bring greater financial inclusion by providing open access for all to fair financial services.
MOTIVATION
Cardano is a project that began in 2015 as an effort to change the way cryptocurrencies are designed and developed. The overall focus beyond a particular set of innovations is to provide a more balanced and sustainable ecosystem that better accounts for the needs of its users as well as other systems seeking integration.
In the spirit of many open source projects, Cardano did not begin with a comprehensive roadmap or even an authoritative white paper. Rather it embraced a collection of design principles, engineering best practices and avenues for exploration. These include the following:
- Separation of accounting and computation into different layers
- Implementation of core components in highly modular functional code
- Small groups of academics and developers competing with peer reviewed research
- Heavy use of interdisciplinary teams including early use of InfoSec experts
- Fast iteration between white papers, implementation and new research required to correct issues discovered during review
- Building in the ability to upgrade post-deployed systems without destroying the network
- Development of a decentralized funding mechanism for future work
- A long-term view on improving the design of cryptocurrencies so they can work on mobile devices with a reasonable and secure user experience
- Bringing stakeholders closer to the operations and maintenance of their cryptocurrency
- Acknowledging the need to account for multiple assets in the same ledger
- Abstracting transactions to include optional metadata in order to better conform to the needs of legacy systems
- Learning from the nearly 1,000 altcoins by embracing features that make sense
- Adopt a standards-driven process inspired by the Internet Engineering Task Force using a dedicated foundation to lock down the final protocol design
- Explore the social elements of commerce
- Find a healthy middle ground for regulators to interact with commerce without compromising some core principles inherited from Bitcoin
From this unstructured set of ideas, the principals working on Cardano began both to explore cryptocurrency literature and to build a toolset of abstractions. The output of this research is IOHK’s extensive library of papers, numerous survey results such as this recent scripting language overview as well as an Ontology of Smart Contracts, and the Scorex project. Lessons yielded an appreciation for the cryptocurrency industry’s unusual and at times counterproductive growth.
First, unlike successful protocols such as TCP/IP, there is little layering in the design of cryptocurrencies. There has been a desire to preserve a single notion of consensus around facts and events recorded in a single ledger, regardless of whether it makes sense.
For example, Ethereum has encumbered enormous complexity attempting to become a universal world computer, but suffers from trivial concerns potentially destroying the system’s ability to operate as a store of value. Should everyone’s program be a first class citizen regardless of its economic value, cost to maintain, or regulatory consequences?
Second, there is little appreciation for prior results in mainstream cryptographic research. For example, Bitshares’ Delegated Proof of Stake could have easily and reliably generated random numbers using coin tossing with guaranteed output delivery, which is a technique known since the 1980s (see the seminal paper by Rabin and Ben-Or).
Third, most altcoins (with a few notable exceptions such as Tezos) have not made any accommodation for future updates. The ability to successfully push a soft or hard fork is pivotal to the long-term success of any cryptocurrency.
As a corollary, enterprise users cannot commit millions of dollars worth of resources to protocols where the roadmap and actors behind them are ephemeral, petty or radicalized. There needs to be an efficient process through which social consensus can form around a vision for evolving the underlying protocol. If this process is enormously burdensome, fragmentation could break the community apart.
Finally, money is ultimately a social phenomenon. In the effort to anonymize and disintermediate central actors, Bitcoin and its contemporaries have also discarded the need for stable identities, metadata and reputation in commercial transactions. Adding these data through centralized solutions removes the auditability, global availability and immutability — which is the entire point of using a blockchain.
Legacy financial systems such as those composed of SWIFT, FIX and ACH are rich in transactional metadata. It is not enough to know how much value moved between accounts, regulation often requires the attribution of actors involved, compliance information, reporting suspicious activity, and other records and actions. In some cases, the metadata is more important than the transaction.
Hence, it seems reasonable to infer that the manipulation of metadata could be as harmful as counterfeiting currency or rewriting transaction history. Making no accommodation for actors who want to voluntarily include these fields seems counterproductive to mainstream adoption and consumer protection.
SOJOURN’S END
The aggregation of our principled exploration of the cryptocurrency space is two collections of protocols. Respectively, a provably secure proof of stake based cryptocurrency called the Cardano Settlement Layer (CSL) and a set of protocols called the Cardano Computation Layer (CCL).
Our design emphasis is to accommodate the social aspects of cryptocurrencies, build in layers by separating the accounting of value from complex computation and address the needs of regulators within the scope of several immutable principles1. Furthermore, where it is sensible, we attempt to vet proposed protocols through peer review and check code against formal specifications.
PROOF OF STAKE

Using proof of stake for a cryptocurrency is a hotly debated design choice, however because it adds a mechanism to introduce secure voting, has more capacity to scale, and permits more exotic incentive schemes, we decided to embrace it.
Our proof of stake protocol is called Ouroboros and it has been designed by an extremely talented team of cryptographers from five academic institutions2 led by Professor Aggelos Kiayias of the University of Edinburgh. The core innovation it brings beyond being proven secure using a rigorous cryptographic model is a modular and flexible design that allows for the composition of many protocols to enhance functionality.
- Overview - Table of Contents
- What Is Cardano?
- Getting Started With Cardano
- How To Get A Cardano Wallet?
- Cardano Resources
- How To Buy Cardano?
- How To Earn Cardano?
- Where To Spend Cardano?
- What Is Cardano Mining?
- Latest Cardano News
This modularity allows for features such as delegation, sidechains, subscribable checkpoints, better data structures for light clients, different forms of random number generation and even different synchronization assumptions.
As a network develops from having thousands to millions and even billions of users, the requirements of its consensus algorithm will also change. Thus, it is vital to have enough flexibility to accommodate these changes and thereby future-proof the heart of a cryptocurrency.
SOCIAL ELEMENTS OF MONEY
Cryptocurrencies are a prime example of the social component of money. When restricting analysis solely to technology, there is little difference between Bitcoin and Litecoin and even less so between Ethereum and Ethereum Classic. Yet, both Litecoin and Ethereum Classic maintain large market capitalizations and robust, dynamic communities as well as their own social mandates.
It can be argued that a large part of the value of a cryptocurrency is derived from its community, the way it uses the currency, and its level of engagement in the currency’s evolution. Furthering the thought, currencies such as Dash have even integrated systems directly into the protocol to engage their community in deciding what should be a priority to develop and fund.
The vast diversity of cryptocurrencies also provides evidence for their social elements. Disagreements about philosophy, monetary policy, or even just between the core developers lead to fragmentation and forks. Yet unlike their cryptocurrency counterparts, fiat currencies of superpowers tend to survive political shifts and local disagreements without a currency crisis or mass exodus.
Therefore, it seems that there are elements of legacy systems that are missing from the cryptocurrency industry. We argue — and have inculcated into the Cardano roadmap – that users of a protocol need incentives to understand the social contract behind their protocol and have the freedom to propose changes in a productive way.
This freedom extends to every aspect of a value exchange system, from deciding how markets should be regulated to which projects should be funded. Yet it cannot be brokered through centralized actors nor require some special credential that could be co-opted by a well funded minority.
Cardano will implement a system of overlay protocols built on top of CSL to accommodate the needs of its users.
First, regardless of the success of a crowdsale to bootstrap development, funds will eventually dissipate. Hence, Cardano will include a decentralized trust3 funded from monotonically decreasing inflation and transaction fees.
Any user should be eligible to request funds from the trust by a ballot system and the stakeholders of CSL vote on who becomes a beneficiary. The process creates a productive feedback loop seen in other cryptocurrencies with treasury/trust systems, such as Dash, by starting a conversation about who should and should not be funded.
Funding discussions force a relation of long and short term goals, the cryptocurrency’s social contract, priorities and the belief in value creation with particular proposals. This conversation means that the community is constantly evaluating and debating its beliefs against possible roadmaps.
Second, our hope is that Cardano will eventually include a formal, blockchain based system to propose and vote on both soft and hard forks. Bitcoin with its block size debate, Ethereum with the DAO fork, and many other cryptocurrencies besides have endured long standing and, in frequent cases, unresolved arguments over the technical and moral direction of the codebase.
It can and should be argued that many of these disagreements, and the fracturing of the community that results when action is taken, are a direct result of a lack of formal processes for debating change.
Where does one go to convince Bitcoin users to adopt Segregated Witness? How should the core developers of Ethereum measure community sentiment for bailing out the DAO? If the community fractures, is the cryptocurrency damaged beyond repair?

In the worst cases, moral authority to act could simply devolve to whoever has the developers, infrastructural relationships and money, not the best wishes of the vast majority of the community. Furthermore, if a large portion of the community is inaccessible or disengaged due to bad incentives4, then how can one truly know if their acts are legitimate?
Proposed cryptocurrencies such as Tezos provide an interesting model to examine where a cryptocurrency protocol is treated like a constitution containing three sections (Transaction, Consensus and Network) with a set of formal rules and process to update the constitution. Yet there remains much work to be done with incentives and over how exactly to model and change a cryptocurrency with a formal language.
The use of formal methods, machine understandable specifications and merging a treasury with this process for financial incentives are being explored as possible avenues for inspiration. Ultimately, just the ability to propose a protocol change in a transparent, censorship free way with blockchain based voting should improve the process, even if more elegant solutions cannot be designed.
DESIGNING IN LAYERS – CARDANO SETTLEMENT LAYER
When designing great protocols and languages, one should not look to the future, but rather to the past. History provides a litany of examples of great ideas that are perfect on paper, yet somehow have not survived, such as the Open Systems Interconnection standards. History also provides happy accidents that have endured from TCP/IP to JavaScript.
Some principles extracted from a historical view are the following:
- You cannot predict the future so build in wiggle room
- Complexity is nice on paper, but simplicity usually wins
- Too many cooks spoil the broth
- Once a standard is set it will probably stick around, regardless of whether it is suboptimal
- Bad ideas can actually evolve into pretty good ones if there is a will
Cardano is a financial system that accepts its social nature. There will be a tremendous need for flexibility and the ability to address arbitrary complexity in a particular user’s transaction. If successful, there will be a need for tremendous computational, storage and network resources to accommodate millions of concurrent transactions.
Yet we do not have a digital, decentralized Robin Hood to take from the rich nodes and give to the poor ones in order to achieve a fair network. Nor do we have the luxury of trusting human beneficence to altruistically sacrifice for the greater good of the network. Therefore, Cardano’s design borrows from TCP/IP the concept of separation of concerns.
Blockchains are ultimately databases ordering facts and events with guarantees about timestamps and immutability. In the context of money, they order ownership of assets. Adding complex computation by storing and executing programs is an orthogonal concept. Do we want to know how much value went from Alice to Bob, or do we want to get involved in figuring out the whole story behind the transaction and deciding how much to send?
It is incredibly tempting to choose the latter as Ethereum has done because it is more flexible, but it violates the design principles above. Figuring out the story means that a single protocol has to be able to understand arbitrary events, script arbitrary transactions, permit arbitration in cases of fraud and even potentially reverse transactions when new information is made available.
Then one has to make difficult design decisions about what metadata to store for each transaction. What elements of the story behind Alice and Bob’s transaction are relevant? Are they relevant forever? When can we throw away some data? Does doing so violate the law in some countries?
- Overview - Table of Contents
- What Is Cardano?
- Getting Started With Cardano
- How To Get A Cardano Wallet?
- Cardano Resources
- How To Buy Cardano?
- How To Earn Cardano?
- Where To Spend Cardano?
- What Is Cardano Mining?
- Latest Cardano News
Furthermore, some computation is private in nature. For example, when calculating the average salary of workers in an office, we would not necessarily want to leak how much each person makes. But what if every computation is publicly known? What if this publicity biases execution order to harm outcome?
Thus, we have chosen the position that the accounting of value should be separated from the story behind why the value was moved. In other words, separation of value from computation. This separation does not mean that Cardano will not support smart contracts. On the contrary, by making the separation explicit, it permits significantly more flexibility in the design, use, privacy and execution of smart contracts.
The value ledger is called the Cardano Settlement Layer (CSL). As the purpose is to account for value, the roadmap has the following goals:
- Support two sets of scripting languages, one to move value and another to enhance overlay protocol support
- Provide support for KMZ sidechains5 to link to other ledgers
- Support multiple types of signature including quantum resistant signatures for higher security
- Support multiple user issued assets
- Achieve true scalability, meaning as more users join, the capabilities of the system increase
SCRIPTING
Starting with the scripting language, transactions between addresses in a ledger require some form of a script to execute and be proven valid. Ideally, one would not want Eve to access Alice’s money, nor would one want a poorly designed script to accidently send value to a dead address making the funds irretrievable.
Systems such as Bitcoin provide an extremely inflexible and draconian scripting language that is difficult to program bespoke transactions in, and to read and understand. Yet the general programmability of languages such as Solidity introduce an extraordinary amount of complexity into the system and are useful to only a much smaller set of actors.
Therefore, we have chosen to design a new language called Simon6 in honor of its creator Simon Thompson and the creator of the concepts that inspired it, Simon Peyton Jones. Simon is a domain-specific language that is based upon Composing contracts: an adventure in financial engineering.
The principal idea is that financial transactions are generally composed from a collection of foundational elements7. If one assembles a financial periodic table of elements, then one can provide support for an arbitrarily large set of compound transactions that will cover most, if not all, common transaction types without requiring general programmability.

The primary advantage is that security and execution can be extremely well understood. Proofs can be written to show correctness of templates and exhaust the execution space of problematic transaction events, such as the creation of new money out of thin air or transaction malleability. Second, one can leave in extensions to add more elements by way of soft forks if new functionality is required.
That said, there will always be a need to connect CSL to overlay protocols, legacy financial systems, and special purpose servers. Thus we have developed Plutus as both a general purpose smart contract language and also a special purpose DSL for interoperability.
Plutus is a typed functional language based on concepts from Haskell, which can be used to write custom transaction scripts. For CSL, it will be used for complex transactions required to add support for other layers we need to connect, such as our sidechains scheme.
SIDECHAINS
With respect to sidechains, Cardano will support a new protocol developed by Kiayias, Miller and Zindros (KMZ sidechains) based upon prior results from proofs of proofs of work. The particular design is beyond the scope of this paper; however, the concept allows for the secure and non-interactive movement of funds from CSL to any Cardano Computation Layer or other blockchain supporting the protocol.
KMZ sidechains are the key to encapsulating complexity. Ledgers with regulatory requirements, private operations, robust scripting languages and other special concerns are effectively black boxes to CSL, yet the CSL user will gain certain guarantees about accounting and the ability to recall funds once computation is complete.
SIGNATURES
In order to securely move value from Alice to Bob, Alice needs to prove she has the right to move the funds. The most direct and reliable way of accomplishing this task is to use a public key signature scheme where funds are connected to a public key and Alice controls an associated private key.
There are hundreds of possible schemes with different security parameters and assumptions. Some rely upon mathematical problems connected to elliptic curves, whereas others are connected to exotic concepts using lattices.
The abstract goal is always the same. There exists a hard problem that cannot be solved unless someone has a secret piece of knowledge. The holder of this piece of knowledge is said to be the owner of the keypair and should be the only entity that has the ability to use it.
There are two groups of concerns a cryptocurrency faces with choosing a signature scheme. First, there is the long-term security durability of the scheme itself. Some cryptographic schemes used in the 1970s and 1980s such as DES have been broken. The period over which the scheme should be expected to survive must be decided upon.
Second, there are many enterprises, governments and other institutions that have preferred, or in some cases, mandated the use of a particular scheme. For example, the NSA maintains the Suite B protocol set. There are standards from ISO and even W3C workgroups on cryptography.
If a cryptocurrency chooses a single signature scheme, it is forced to accept that the scheme could be broken at some point in the future and at least one entity cannot use the cryptocurrency due to legal or industry restrictions. Yet a cryptocurrency cannot support every signature scheme as this would require every client to understand and validate each scheme.
For Cardano, we decided to start with using elliptic curve cryptography, the Ed25519 curve in particular. We also decided to enhance the existing libraries by adding support for HD wallets using Dr Dmitry Khovratovich and Jason Law’s Specification.
This said, Cardano will support more signature schemes in the future. In particular, we are interested in integrating BLISS-B to add quantum computer resistant signatures to our system. We are also interested in adding SECP256k1 to enhance interoperability with legacy cryptocurrencies such as Bitcoin.
Cardano has been designed with special extensions that will allow us to add more signature schemes through a soft fork. They will be added as needed and during major updates planned in the roadmap.
USER ISSUED ASSETS (UIAS)
Early in Bitcoin’s history, protocols were quickly developed to allow users to issue assets that piggybacked on Bitcoin’s accounting system in order to track multiple currencies concurrently. These protocols were not natively supported by the Bitcoin protocol, but implemented through clever hacks.
In the case of Bitcoin overlays such as Colored Coins and Mastercoin (now called Omni), light clients are forced to rely on trusted servers. Also transaction fees still have to be paid in bitcoins. These properties combined with the single pipeline for transaction approval make Bitcoin suboptimal for multi-asset accounting.
- Overview - Table of Contents
- What Is Cardano?
- Getting Started With Cardano
- How To Get A Cardano Wallet?
- Cardano Resources
- How To Buy Cardano?
- How To Earn Cardano?
- Where To Spend Cardano?
- What Is Cardano Mining?
- Latest Cardano News
In the Ethereum case using the ERC20 standard, there is more feature richness. However, transaction fees still require ether. Furthermore, the Ethereum network is having difficulty scaling to the needs of all the issued ERC20 tokens.
The fundamental problem can be broken into three parts: resources, incentives and concern. With respect to resources, adding an entirely new currency to the same ledger means one has two independent UTXO (unspent transaction inputs) sets sharing the bandwidth, mempool and block space.
Consensus nodes responsible for embedding transactions of these currencies need an incentive for doing so. And not every user of a cryptocurrency will or should care about a particular entity’s currency.
Given these problems, the benefits are tremendous as the primary token of a multiasset ledger can effectively serve as a bridge currency allowing for decentralized market making. Special purpose assets could be issued to provide additional utility such as value stable assets like Tether or MakerDAO that are useful for lending and remittance applications.
Given the challenges, Cardano has adopted a pragmatic approach to multiasset accounting. Building in stages, the first challenge is designing the necessary infrastructure to support the demands of thousands of UIAs. Namely the following advancements are necessary:
- Special purpose authenticated data structures to permit the tracking of a very large UTXO state
- The ability to have a distributed mempool to hold a huge set of pending transactions
- Blockchain partitioning and checkpoints to permit a huge global blockchain
- An incentive scheme that rewards consensus nodes for including different sets of transactions
- A subscription mechanic that allows users to decide which currencies they want to track
- Strong security guarantees that UIAs enjoy similar security as the native asset
- Support for decentralized market making to improve liquidity between UIA and the primary token
Our preliminary efforts for finding the right authenticated data structure have resulted in a new type of AVL+ Tree jointly developed by Leo Reyzin, IOHK and Waves. More research is required, but it is a foundational advancement that will be included in a later version of Cardano.
A distributed mempool could be implemented using Stanford University’s RAMCloud protocol. Experiments will begin in Q3 of 2017 to study its integration into Cardano’s consensus layer.
The remaining topics are interconnected and covered by ongoing research. We expect — subject to research results — to include a protocol into Cardano for UIAs during the Basho of CSL release in 2018.
SCALABILITY
Distributed systems are composed of a set of computers (nodes) agreeing to run a protocol or suite of protocols to accomplish a common goal. This goal could be sharing a file as defined by the BitTorrent protocol or folding a protein using Folding@Home.
The most effective protocols gain resources as nodes join the network. A file hosted by BitTorrent, for example, can be downloaded much faster on average if many peers are concurrently downloading it. The speed increases because the peers provide resources while also consuming them. This characteristic is what one typically means when stating a distributed system scales.
The challenge with the design of all current cryptocurrencies is that they actually are not designed to be scalable. Blockchains, for example, are usually an append-only linked list of blocks. The security and availability of a blockchain protocol relies upon many nodes possessing a full copy of the blockchain data. Thus, a single byte of data must be replicated among N nodes. Additional nodes do not provide additional resources.

This result is the same for transaction processing and the gossiping of messages throughout the system. Adding more nodes to the consensus system does not provide additional transaction processing power. It just means more resources have to be spent to do the same job. More network relaying meaning more nodes have to pass the same messages to keep the whole network in synchronization with the most current block.
Given this topology, cryptocurrencies cannot scale to a global network on par with legacy financial systems. In contrast, legacy infrastructure is scalable and has orders of magnitude for more processing and storage power. Adding a specific point, Bitcoin is a very small network relative to its payment peers, yet struggles to manage its current load.
Our scalability goals for Cardano are greatly aided by our consensus algorithm. Ouroboros permits a decentralized way to elect a quorum of consensus nodes, which in turn can run more traditional protocols developed over the last 20 years to accommodate the needs of large infrastructure providers such as Google and Facebook10.
For example, the election of a quorum for an epoch means we have a trusted set of nodes to maintain the ledger for a specific time period. It is trivial to elect multiple quorums concurrently and partition transactions to different quorums.
Similar techniques could be applied for network propagation and also sharding the blockchain itself into unique partitions. In our current roadmap, scaling methods will be applied to Ouroboros starting in 2018 and continue to be a focus in 2019 and 2020.
CARDANO COMPUTATION LAYER
As mentioned previously, there are two components of a transaction: the mechanism to send and record the flow of tokens and the reasons as well as conditions behind moving tokens. The latter can be arbitrarily complex and involve terabytes of data, multiple signatures and special events occurring. The latter can also be remarkably simple with a single signature pushing value to another address.
The challenge behind modeling the reasons and conditions of value flow is that they are immensely personal to the entities involved in the most unpredictable of ways. Lessons from contract law paint an even more problematic picture where the actors themselves might not even be aware that the transaction does not match commercial reality. We generally call this phenomenon “the semantic gap”11.
Why should one build a cryptocurrency chasing an endless layer of complexity and abstraction? It seems Sisyphean in nature and naive in practice. Furthermore, each abstraction embraced has both legal and security consequences.
- Overview - Table of Contents
- What Is Cardano?
- Getting Started With Cardano
- How To Get A Cardano Wallet?
- Cardano Resources
- How To Buy Cardano?
- How To Earn Cardano?
- Where To Spend Cardano?
- What Is Cardano Mining?
- Latest Cardano News
For example, there are numerous activities online that are universally deemed illegal or scorned such as the trafficking of child pornography or the selling of state secrets. By deploying robust decentralized infrastructure, one is now providing a channel for this activity to occur with the same censorship resistance that normal commercial transactions enjoy.
It is legally unclear if the consensus nodes of the network — which have the incentive to become more federated over time to promote efficiency — would be held accountable for the content they host.
Prosecution of Tor operators, the brutal treatment of Silk Road’s operator and the lack of overall legal clarity behind legal protections of protocol participants leaves an uncertain road. There is no lack of imagination of what else a sufficiently advanced cryptocurrency could enable (see the Ring of Gyges). Is it reasonable to force all users of a cryptocurrency to endorse or at least enable the worst acts and conduct of the web?
Unfortunately, there are no clear answers that provide insight to a cryptocurrency designer. It is more about picking a position and defending its merit. The advantage that both Cardano and Bitcoin have is that we have chosen to separate concerns to layers. With Bitcoin, there is Rootstock. With Cardano, there is the Cardano Computation Layer.
The kinds of complex behavior that would enable the acts elaborated previously cannot run on CSL. They require the ability to run programs written in a Turing complete language and some form of gas economics to meter computation. They also require consensus nodes willing to include the transactions in their blocks.
Thus, a functionality restriction could reasonably protect users. So far, most established governments have not taken the position that the use or maintenance of a cryptocurrency is an illegal act. Hence, the vast majority of users should be comfortable maintaining a ledger that is comparable in capability with a digital payment system.
When one wants to extend capability, there are two possibilities. It is enabled by a private collective of likeminded individuals and ephemeral in nature (for example, a poker game). Or, it is enabled by a ledger of comparable capabilities as Ethereum. In both cases, we have chosen outsourcing the events to another protocol.
In the case of a private, ephemeral event, it is reasonable to avoid the blockchain paradigm entirely, but rather restrict efforts towards a library of special purpose MPC protocols that can be invoked when desired by a group of likeminded participants. The computations and activities are coordinated in a private network and reference CSL only as a trusted bulletin board and a message passing channel when necessary.
The key insight in this case is that there is consent, encapsulation of liability and privacy. CSL is being used as a digital commons for users to meet and communicate — like a park would host a private event — but does not provide any special accommodations or facilitation. Furthermore, the use of special purpose MPC will enable low latency interaction without the need for blockchain bloat. Thus, it improves the scale of the system.
Cardano’s research efforts towards this library are centralized at our Tokyo Tech laboratory with some assistance from scientists abroad. We call the library “Tartaglia” after a fellow mathematician as well as contemporary of Cardano and expect the first iteration to be available in Q1 of 2018.
In the second case, one needs a blockchain with a virtual machine, a set of consensus nodes and a mechanism to enable communication between the two chains. We have begun the process of rigorously formalizing the Ethereum Virtual Machine using the K-framework12 in partnership with a team from the University of Illinois.
The result of this analysis will inform the most optimal way to design a replicated and eventually distributed virtual machine13 with clear operational semantics and strong guarantees of correct implementation from the specification. In other words, the VM actually does what the code tells it to do with the security risks minimized.
There are still unresolved questions about the gas economics proposed by Ethereum and how it relates to work such as Jan Hoffmann et al’s resource aware ML and the broader study of resource estimation for computation. We are also curious about the level of language independence of the virtual machine. For example, the Ethereum project has expressed desire for transition from their current VM to Web Assembly.
The next effort is in developing a reasonable programming language to express stateful contracts that will be called as services by decentralized applications. For this task, we have chosen both the approach of supporting the legacy smart contract language Solidity for low assurance applications and developing a new language called Plutus for higher assurance applications requiring formal verification.
Like the solidity based Zeppelin project, IOHK will also develop a reference library of Plutus code for application developers to use in their projects. We will also develop a specialized set of tools for formal verification inspired by work from UCSD’s Liquid Haskell project.
In terms of consensus, Ouroboros was designed in a sufficiently modular fashion to support smart contract evaluation. Hence, both CSL and CCL will share the same consensus algorithm. The difference is that Ouroboros can be confirmed to permit both permissioned and permissionless ledgers via token distribution.
With CSL, Ada has been distributed by a token generating event to purchasers throughout Asia who will eventually resell on a secondary market. This means that CSL’s consensus algorithm is controlled by a diverse and increasingly more decentralized set of actors or their delegated assigns. With CCL, it is possible to create a special purpose token held by delegates of that ledger who could be regulated entities, thereby creating a permissioned ledger.
The flexibility of this approach allows for different instances of CCL to materialize with different rules about the evaluation of transactions. For example, gambling activities could be restricted unless KYC/AML data is present simply by blacklisting non-attributed transactions.
Our final design focus is on adding trusted hardware security modules (HSM) to our protocol stack. These are two enormous advantages when introducing these capabilities into the protocol. First, HSMs provide massive boosts in performance14 without introducing security concerns beyond trusting the vendor. Second, through the use of Sealed Glass Proofs (SGP), HSMs can provide assurances that data can be verified and then destroyed without being copied or leaked to malicious outsiders.
Focusing on the second point, SGPs could have a revolutionary impact upon compliance. Ordinarily, when a consumer provides personally identifiable information (PII) to authenticate identity or prove the right to participate, this information is handed to a trusted third party with the hope it will not act maliciously. This activity is intrinsically centralized, the data provider loses control over their PII and is also subject to various regulations based on jurisdiction.
The ability to select a set of trusted attestors and then warehouse PII in a hardware enclave means that any actor with a sufficiently capable HSM will be able to verify facts about an actor in an unforgeable way without the verifier knowing the identity of the actor. For example, Bob is not an US citizen. Alice is an accredited investor. James is a US taxpayer and one should send taxable profits to account X.
Cardano’s HSM strategy will be to attempt implemented specialized protocols over the next two years using Intel SGX and ARM Trustzone. Both modules are built into billions of consumer devices from laptops to cellphones and require no additional effort on the consumer side to use. Both are also heavily vetted, well designed and based upon years of iteration from some of the largest and best funded hardware security teams.
REGULATION
The harsh reality of all modern financial systems is that as they scale, they accumulate a need, or at least a desire, for regulation. This outcome is generally the result of recurrent collapses due to the negligence of some actor or cabal of actors in a marketplace.
For example, the Knickerbocker Crisis of 1907 resulted in the creation of the Federal Reserve System in 1913 as a lender of last resort. Another example is the excesses of the 1920s in the United States that resulted in a terrible financial collapse, the Great Depression. This collapse yielded the creation of the Securities Exchange Commission in 1934 in order to prevent a similar event or at least hold bad actors accountable.
- Overview - Table of Contents
- What Is Cardano?
- Getting Started With Cardano
- How To Get A Cardano Wallet?
- Cardano Resources
- How To Buy Cardano?
- How To Earn Cardano?
- Where To Spend Cardano?
- What Is Cardano Mining?
- Latest Cardano News
One can reasonably debate the need for, scope and efficacy of regulation, but one cannot deny its existence and the zeal with which major governments have enforced it. However, the challenge all regulators face as the world globalizes and cash becomes digital is two-pronged.
First, which set of regulations should be supreme when dealing with a collection of jurisdictions? The antiquated notion of Westphalian sovereignty melts when a single transaction can touch three dozen countries in under a minute. Should it simply be whomever wields the most geopolitical influence?
Second, improvements in privacy technology have created a digital arms race where it will become increasingly more difficult to even understand who has participated in a transaction, much less who owns a particular store of value. In a world where millions of dollars of assets can be controlled with nothing more than a secretly held 12-word mnemonic15, how do you enforce effective regulation?
Like all financial systems, the Cardano protocol must have an opinion in its design over what is fair and reasonable. We have chosen to divide between individual rights and the rights of a marketplace.
Individuals should always have sole access to their funds without coercion or civil asset forfeiture. This right has to be enforced because not all governments can be trusted not to abuse their sovereign power for the personal gain of corrupt politicians, as seen in Venezuela and Zimbabwe. Cryptocurrencies have to be engineered to the lowest common denominator.
Second, history should never be tampered with. Blockchains provide a promise of immutability. Introducing the power to roll back history or alter the official record introduces too much temptation to change the past in order to benefit a particular actor or actors.
Third, the flow of value should be unrestricted. Capital controls and other artificial walls diminish human rights. Outside of the futility of attempting to enforce them16, in a global economy with many citizens in the least developed nations traveling outside of their jurisdiction to find a living wage, restricting capital flows usually ends up harming the poorest in the world.
These principles stated, markets are distinctly different from individuals. While the designers of Cardano believe in individual rights, we also believe that markets have the right to openly state their terms and conditions, and if an individual agrees to do business within this market, then they must be held to those standards for the sake of integrity of the entire system.
The challenge has always been cost and practicality of enforcement. Small, multijurisdictional transactions are simply too expensive in legacy systems to provide high assurance of recourse in the event of fraud or a commercial dispute. When one sends their wire transfer to the Nigerian Prince17, it is usually too expensive to try to get one’s funds back.
For Cardano, we feel we can innovate on three levels. First, through the use of smart contracts the terms and conditions of commercial relationships can be better controlled. If all assets are digital and can be solely expressed on CSL, strong guarantees of fraud-free commerce can be gained.
Second, the use of HSMs to provide an identity space where PII is not leaked but yet used to authenticate and credential actors should provide a global reputation system and allow for much lower cost regulated activities to be conducted, such as online gaming with automated tax compliance or decentralized exchanges.
Finally, in Cardano’s roadmap is the creation of a modular regulation DAO that can be customized to interact with user written smart contracts in order to add mutability, consumer protection and arbitration. The scope of this project will be outlined in a later paper.
Getting Started With Cardano
Cardano has been a marathon project involving feedback from hundreds of the brightest minds inside and outside of the cryptocurrency industry. It involves tireless iteration, the active use of peer review, and shameless theft of great ideas when uncovered.
The remaining sections each cover a particular aspect of focus we have decided is a core component of our project. Some were selected due to a desire to improve the overall best practices of the space whereas others are specific to Cardano’s evolution.
While no project can cover every goal or satisfy every user, our hope is to provide a vision for what a self-evolving financial stack should look like for jurisdictions that lack them. The ultimate reality of cryptocurrencies is not that they will disrupt the existing legacy financial systems. Legacy financial systems are always capable of absorbing change and maintaining their form and function.
Rather one ought to look to places where it is simply too expensive to deploy the existing banking system, where many live on less than a few dollars a day, have no stable identity and credit is impossible to find.
In these places, the power to bundle a payment system, property rights, identity, credit and risk protection into a single application running on a cell phone is not just useful, it is life changing. The reason we are building Cardano is that we feel we have a legitimate shot at delivering — or at least advancing — this vision for the developing world.
If we can change the way cryptocurrencies are designed, evolved and funded, then there is a great accomplishment.
THE ART OF ITERATION
Cryptocurrencies are protocols implemented as software. Protocols are simply intelligent conversations between participants. Software is ultimately the manipulation of data given some goal. Yet the difference between solid, reliable software as well as useful, secure protocols and their converse is completely human.
Good software needs accountability, clear business requirements, repeatable processes, thorough testing and tireless iteration. Good software also needs reasonably talented developers with enough domain specific knowledge to properly design a system that can fully resolve whatever problem they are trying to solve.
As for useful and secure protocols, especially ones involving cryptography and distributed systems, they start in a more academic and standards driven process. Peer review, endless debates and a firm concept of trade offs are necessary to ensure a protocol is useful. Yet these alone are not sufficient, protocols need to be implemented and tested by real life use.
The unique challenge in the cryptocurrency industry is that two completely different philosophies are mangled together without a proper Hegelian synthesis. Our thesis is a “move fast and break things” startup mentality driven by youth, greed and passion. The antithesis is a slow, methodical and academically oriented approach motivated by a desire to solidify the innovations of our space into a nice niche enjoying ample funding and prestige.
The result is that many cryptocurrencies are either entirely specified on a white paper only relevant to a CV or just by hastily written code. None of the current top ten18 cryptocurrencies by market capitalization are based upon a peer reviewed protocol. None of the current ten top cryptocurrencies were implemented from a formal specification.
Yet billions of dollars of value are at stake. Once deployed, a cryptocurrency is exceedingly difficult to change. How does a user know they are using a secure system? How does a user know that the marketing claims are legitimate? What if the proposed protocol can never achieve the claims
?
This lack of synthesis and respect for process is one of the primary reasons IOHK wanted to build Cardano. Our hope was to develop a reference project that would serve as an example of how to do things in a more effective, sane and honest way.
The goal is not to propose a totally new way of developing software and protocols, but rather to acknowledge that great software and protocols already exist and we can mimic the conditions that led to their creation. Second, to make these conditions publicly known and open source if possible so that they can be imitated for the benefit of the entire field.
FACTS AND OPINIONS
The other concern is over where facts end and opinion begins. There are hundreds of programming languages, dozens of development paradigms and more than one philosophy on project management. The academic world is riddled with its own challenges stemming from its distance from business concerns and practicality
For Cardano, we first attempted to capture obvious deficiencies that can be universally agreed to be useful from an engineering perspective. For example, cryptography and distributed systems are both extraordinarily involved topics with far too many examples of how naive hands can make horrific mistakes.
- Overview - Table of Contents
- What Is Cardano?
- Getting Started With Cardano
- How To Get A Cardano Wallet?
- Cardano Resources
- How To Buy Cardano?
- How To Earn Cardano?
- Where To Spend Cardano?
- What Is Cardano Mining?
- Latest Cardano News
Therefore, any protocol requiring insight from these domains needs to be designed by an acknowledged expert and be submitted for review by other experts.
Ouroboros is our first case study of this area. It was designed by a team of cryptographers with a large, diverse and publicly verifiable publication history. It was built according to the standard cryptography process, with security assumptions, an adversarial model and proofs.
These proofs were checked by submission to conferences20 and also independently by computer proofs written in Isabelle by a team at the University of Cambridge.
Yet this work alone provides no guarantees of usefulness — just a rigorous check of a security model given some assumptions. For usefulness, one needs to implement and test the protocol. Our developers have done so in both Haskell and also Rust. This work revealed that more effort needed to be focused on the synchronization model, which led to the creation of Ouroboros Praos.
This art of iteration is what produces great protocols, with each step leading to new lessons and a requirement to re-verify the correctness of prior step. It is costly, time consuming, and at times truly tedious, yet it is required to ensure a protocol is correctly designed.
Protocols — especially ones to be used by billions of people — are not short lived and rapidly evolving. Rather they are intended to be followed for years to decades. It seems entirely reasonable that, prior to burdening the world with a new financial system we all have to live with for the next 100 years, we want to demand some tedium and rigor from its designers.
FUNCTIONAL SINS
Moving into more opinionated territory, the tools, languages and methodologies used in software development are more artifacts of religious providence than objective reality. Source code is like written prose. Everyone has an opinion of what is good — and what is being communicated is, at times, less important than how it is communicated.
We must commit the sin of choosing a side accepting that it will be wrong in at least one person’s eyes. However, there is at least a large corpus of justification behind our choice.
The protocols making Cardano possible are being implemented in Haskell. The user interface has been encapsulated in a fork of Electron that we are calling Daedalus. We have chosen to use the web architectural model where possible, and for our database, we opted for a key-value paradigm using RocksDB.
From a component level, this abstraction means that maintenance is far simpler, better technology can be substituted later with little effort, and that our stack is partly tied to the development efforts of Github and Facebook.
Using a WebGuI allows us to leverage React and develop front end features using tools understood by hundreds of thousands of JavaScript developers. Using a web architecture means that components can be treated as services and the security model is sensible.
Choosing Haskell for protocol development was the most difficult choice. Even in the functional world, there are ample choices. On the more flexible and impure side, there are languages like Clojure, Scala and F#, which benefit from the enormous libraries of Java and the .Net ecosystems while preserving some of the best aspects of functional programming.
There are more academically oriented languages such as Agda and Idris that have a close connection to techniques that would allow for strong verification of correctness. Yet they lack reasonable libraries and have a subpar development experience.
For Cardano, the choice came down to Ocaml and Haskell. Ocaml is a wonderful language with a great community, good tooling, reasonable development experience and a great legacy in the formal verification space through Coq23. So why did we choose Haskell?
WHY HASKELL?

The protocols that compose Cardano are distributed, bundled with cryptography and require a high degree of fault tolerance. On the best days, there will still be Byzantine actors, malformed messages and faulty clients unintentionally causing some form of havok on the network.
First, we wanted a language that enjoys a strong type system where we could easily use tools such as Quickcheck and more elaborate techniques such as Refinement Types while having a reasonable expectation of fault tolerance. An Erlang style OTP model satisfies the latter whereas languages like Haskell and Ocaml satisfy the former.
With the introduction of Cloud Haskell, Haskell gained many of Erlang’s advantages while not surrendering its own. Furthermore, Haskell’s modularity and composability has allowed us to use a lighter weight bespoke library called Time Warp for Cardano.
Second, Haskell’s libraries have evolved greatly over the last few years thanks to extensive work of commercial entities like Galois, FP Complete and Well-Typed. As a consequence, Haskell can be used to write production applications.
Third, PureScript’s rapid evolution has provided a much needed bridge to the JavaScript world akin to what Clojurescript has given Clojure. We expect PureScript will be especially important when it comes to getting Cardano to work in a browser and developing mobile wallets.
Fourth, with respect to dependency resolution, Haskell in the last several years has enjoyed a significant social and technological effort led by technologists like Michael Snoyman through a platform called stackage that is both easy to use and well supported by FP Complete.
Fifth, beyond adequate dependency resolution, we aim for our software builds to be reproducible. In other words, with the same configuration values and dependency versions it should produce exactly the same build artifacts. Through stackage, we have been using NixOps to achieve reproducibility with great success.
Finally, the talent pool of developers specializing in Haskell is reasonably large — compared to its peers — and quite well-trained with the right mix of academic and industry credentials. It also acts as a competency filter as it is uncommon to find experienced Haskell developers without detailed knowledge of computer science.
FORMAL SPECIFICATION AND VERIFICATION
A significant strength of developing a protocol using a provably correct security model is that it provides a guaranteed limit of adversarial power. One is given a contract that as long as the protocol is followed and the proofs are correct, the adversary cannot violate the security properties claimed.
Deeper reflection makes the prior assertion even more significant. Adversaries can be arbitrarily intelligent and capable. To say they are defeated solely through a mathematical model is extraordinary. And, of course, it is not entirely true.
Reality introduces factors and circumstances that prevent the utopia of pure security and correct behavior from existing. Implementations can be wrong. Hardware can introduce attack vectors previously unconsidered. The security model might be insufficient and not conform to real life use.
A judgement call is needed about how much specification, rigor and checking is demanded for a protocol. For example, endeavors like the SeL4 Microkernel project are a prime example of an all out assault on ambiguity requiring almost 200,000 lines of Isabelle code to verify less than 10,000 lines of C code. Yet an operating system kernel is critical infrastructure that could be a serious security vulnerability if not properly implemented.
Should all cryptographic software require the same Herculean effort? Or can one choose a less vigorous path that produces equivalent outcomes? Also does it matter if the protocol is perfectly implemented if the environment it runs in is notoriously vulnerable such as on Windows XP?
For Cardano, we have chosen the following compromise. First, due to the complex nature of the domains of cryptography and distributed computing, proofs tend to be very subtle, long, complicated and sometimes quite technical. This implies that human driven checking can be tedious and error-prone. Therefore, we believe that every significant proof presented in a white paper written to cover core infrastructure needs to be machine checked.
Second, to verify Haskell code so it correctly corresponds to our white papers, we can choose between two popular options: interfacing with SMT provers via LiquidHaskell and using Isabelle/HOL.
- Overview - Table of Contents
- What Is Cardano?
- Getting Started With Cardano
- How To Get A Cardano Wallet?
- Cardano Resources
- How To Buy Cardano?
- How To Earn Cardano?
- Where To Spend Cardano?
- What Is Cardano Mining?
- Latest Cardano News
SMT (satisfiability modulo theories) solvers deal with the problem of finding functional parameters that satisfy an equation or inequation, or alternatively showing that such parameters do not exist. As discussed by De Moura and Bjørner, use cases of SMT are various, but the key point is that these techniques are both powerful and can dramatically reduce bugs and semantic errors.
Isabelle/HOL, on the other hand, is a more expressive and diverse tool which can be used to both specify and verify implementation. Isabelle is a generic theorem solver working with higher-order logic constructs, capable of representing sets and other mathematical objects to be used in proofs. Isabelle itself integrates with Z3 SMT prover to work with problems involving such constraints.
Both approaches provide value and therefore we have decided to embrace them both in stages. Human written proofs will be encoded in Isabelle to check their correctness thereby satisfying our machine checking requirement. And we intend on gradually adding Liquid Haskell to all production code in Cardano’s implementation throughout 2017 and 2018.
As a final point, formal verification is only as good as the specification one is verifying from and the toolsets available. One of the primary reasons for choosing Haskell is that it provides the right balance of practicality and theory. Specification derived from white papers looks a lot like Haskell code, and connecting the two is considerably easier than doing so with an imperative language.
There is still enormous difficulty in capturing a proper specification and also updating the specification when changes such as upgrades, bug fixes and other concerns need to be made; however, this reality does not in any way diminish the overall value. If one is going to trouble of building a foundation upon provable security, then the implementation should be what was actually proposed on paper.
TRANSPARENCY
A final question when discussing the science and engineering of developing a cryptocurrency is how to address transparency. Design decisions are not Boolean and ethereal, coming to developers in dreams and then suddenly becoming cannon. They are derived from experience, debate and lessons learned from earlier mistakes.
The challenge is that a totally transparent development process could influence discussion to become more theatrical than evidence based. Egos, attempts to win over a community, and fear of sounding stupid could force conversations to become sterile and counter productive.
Furthermore, outsiders could attempt to co-opt the conversation in an effort to force their particular tangent to become the only relevant topic. Everyone has a sacred cow.
So how does one balance the need for a transparent development process, which is owed to the community that has entrusted progress to a set of core developers, with the need for freedom of expression without fear?
With Cardano, we have decided to embrace a standards driven process with directed oversight. The community needs to know that the science and the code are well thought out, checked and actually solve the things that developers claim they do. To this end, peer review should completely satisfy the science component as it has been designed specifically for this purpose and has given us the modern world.
For code, this topic is a bit more opinionated. For Cardano, we have elected to entrust the Cardano Foundation to serve as a final auditor of IOHK’s work. In particular, they are entrusted with the following duties:
1. Regular review of the source code contained in the Cardano Github to check for quality, test coverage, proper comments and completeness
2. Review of all Cardano documentation for correctness and usefulness
3. Verifying the claims that the protocols produced by the scientists are fully implemented
To accomplish this task, IOHK will submit regular and timely reports to the Foundation – and its assigns – to review. The Foundation in turn will release a development oversight report to the Cardano community on at least a quarterly basis.
This first effort is intended to start a broader conversation about how a decentralized project achieves accountability. Development oversight from a trusted third party is a powerful tool to ensure that developers are on track, but it is not sufficient to completely guarantee that the project will always deliver.
For this reason, after the treasury is integrated into CSL, the Foundation will encourage additional development teams to construct alternative clients based upon the formal specifications developed jointly with IOHK. Development diversity has been a great technique used by the Ethereum project to avoid a monoculture forming around a single set of ideas or developers.
With respect to specifications, there is a wealth of knowledge to be gained from the standards process followed by the WC3 and the IETF. Ultimately, each protocol Cardano integrates requires a specification that is independent of academic work or source code. Rather it needs to be in a suitable format such as an RFC.
One of the Cardano Foundation’s core tenets is to act as standards body specifically for the Cardano protocols and to host conversations to update, add or change standards relevant to Cardano. If the internet (a product of standards) through IETF can reach consensus about what core protocols shall be used, then it is entirely reasonable to assume that a dedicated body could facilitate the same outcome.
As a closing note, it is interesting to explore moving these discussions to a decentralized entity hosted on a blockchain. This concept is called a decentralized autonomous organization (DAO) and preliminary work is underway in this area. IOHK will develop a reference DAO model for entities interfacing with Cardano to use if desired and it is the Cardano Foundation’s prerogative to decide whether to embrace it under their standards mandate.
How To Get A Cardano Wallet?
To use Ada you must download Daedalus. Daedalus is a secure, multi-platform, HD (hierarchical deterministic) wallet for the Ada cryptocurrency. Install Daedalus on your computer and open the application. Watch the Daedalus tutorial video if you require help to set up your digital wallet:
Now you can send and receive Ada, and view a history of the transactions you have made. For more information about Ada transactions that have taken place and about the Cardano blockchain itself, you can use the Cardano Block Explorer.
This specially built tool can be used to search for transactions. You can also see information about the state of blockchain, for example about its slots and epochs. Beyond being used to send and receive Ada, the Daedalus wallet has many special features, which make it easy to use and give you a high degree of confidence about its security. These include:
- Encrypted private keys and spending passwords, offering protection against security threats such as malware.
- Wallets can be exported to paper certificates, giving the maximum security option of placing funds in cold storage.
- Ada redemption is built directly into Daedalus and supports encrypted and unencrypted redemption certificates.
- Configurable transaction assurance level monitoring, allowing users to be sure when transactions become irreversible.
Engineers are in the process of designing and building many more useful features. Plans for development include:
- Ethereum Classic and Bitcoin support.
- A mobile wallet for Android and iOS.
- Staking, which enables Ada holders to participate in the block generation process, and earn more of the currency.
- An application store with community-built applications and support for virtually any cryptocurrency.
Cardano Resources
- Cardano Twitter
- Cardano Mail
- Cardano Github
- Cardano Blockchain Explorer
- Cardano Launch
- Cardano Documentation
- Cardano Roadmap
- Cardano Testnet
- Cardano SL Source
- Cardano Foundation
- Cardano Hub
- Cardano Foundation YouTube
- Cardano Foundation Twitter
- Cardano Slack
- Cardano Reddit
- Cardano Community
- Daedalus Platform
- IOHK
- IOHK blog
- IOHK YouTube
How To Buy Cardano?
You can buy, sell or trade Ada through digital currency exchanges like BITTREX. Below is a list of exchanges that currently list Ada, many more will be added over the coming months. Future exchange partnerships will be announced via our social media channels.
Ada will also be available at a network of ATM machines in Japan. Starting with five locations, the network is planned to grow to about 25 ATMs within a year of Ada’s launch. A list of ATM locations will be added here as they become operational.
Buy ADA(Cardano) from CoinSwitch
1. Select BTC on the top and ADA on the bottom, enter the amount of BTC you want to exchange. This will show the quantity of ADA at current exchange rate. Now you have to click ‘View Rates On All Exchanges’ button.
(The amount displayed here may differ with the actual amount which you will receive after the conversion.)
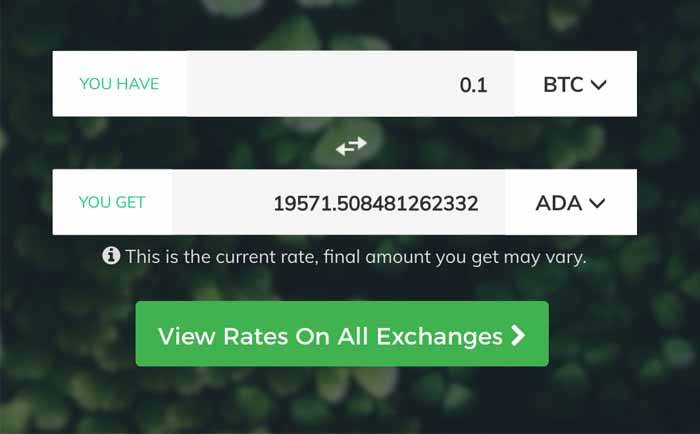
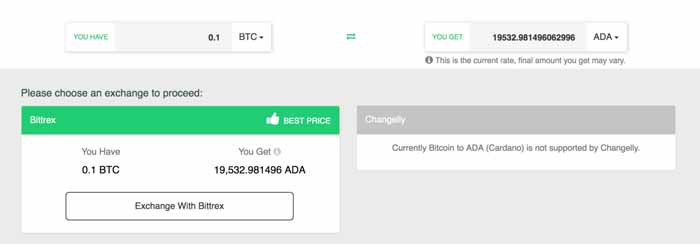
2.Here you will see the list of all exchanges with ADA quantity. Choose the best exchange to convert BTC to ADA or choose the one recommended by us.
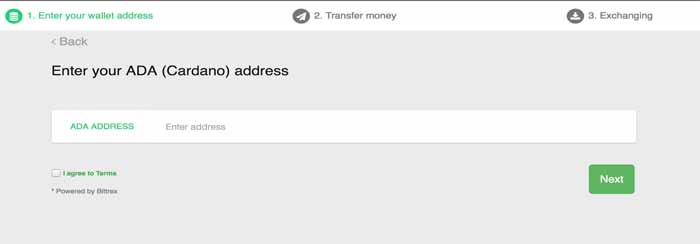
3. Provide your ADA wallet address. You will receive your ADA tokens in that wallet. Please double check the address and read the terms before hitting Next button. If you don’t have ADA wallet the you can setup one from https://daedaluswallet.io/
4. Here it will show the BTC address of the exchange. Now you have to send BTC from your wallet to that address.

5. Once the exchange will receive your BTC then it will initiate the ADA conversion.
You can always track your transaction on the block chain with our easy to access links, below is your transactions status.
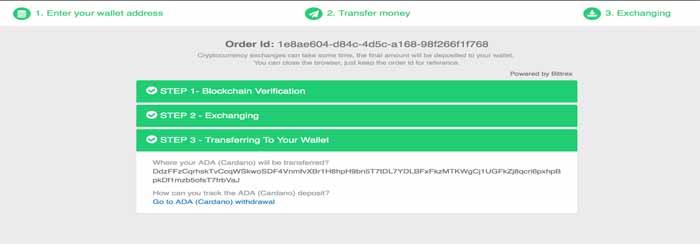
Here you go! The transaction is now completed, and now you can check your ADA wallet. Note that although the transaction is finished, in some cases your wallet needs some additional confirmations to display the received funds. All you should do is to just wait until your coins are displayed.
How To Earn Cardano?
There are now many different cryptocurrencies and the industry continues to see companies and governments experimenting with and starting to implement blockchain technology, whether it be for efficiencies through permissioned blockchains or through decentralized solutions.
- Overview - Table of Contents
- What Is Cardano?
- Getting Started With Cardano
- How To Get A Cardano Wallet?
- Cardano Resources
- How To Buy Cardano?
- How To Earn Cardano?
- Where To Spend Cardano?
- What Is Cardano Mining?
- Latest Cardano News
Cardano differentiates itself by being designed from the ‘ground up’ to deliver a secure and sustainable blockchain that can protect user privacy whilst allowing for regulation. Cardano aims to be a mature blockchain that is ready for large scale applications.
Technological Innovation
- Cardano is the first protocol to incorporate Ouroboros, the ground breaking proof of stake algorithm. The IOHK team employed a “first-principles” approach, driven by peer-reviewed academic research to build Cardano from the ground up.
- This uniquely collaborative effort steadily constructed the most precisely engineered cryptocurrency yet, a product that brings together such disciplines as distributed systems, mechanism design and cryptography. The result is the first cryptocurrency to be based in Haskell code, an industrial strength product that delivers the resilience necessary for mission-critical systems, in this case, securing investment.
- Cardano’s multi-layer protocol performs advanced functions, and has at its foundation a settlement layer that is elegantly linked to a control layer. The settlement layer will have a unit of account, while the control layer will run smart contracts and will be programmed to recognise identity, assisting compliance (and allowing blacklisting, for instance).
- The protocol is geared towards protecting privacy rights of users, while also taking into account the needs of regulators. In doing so, Cardano is the first protocol to balance these requirements in a nuanced and effective way, pioneering a new approach for cryptocurrencies.
- The system is designed so that it can be upgraded by way of soft forks, enabling it to adapt to changing needs and evolve quickly, when required. A treasury system is also being installed that will ensure the sustainability of the protocol. Completely open source and patent-free, Cardano is built in the spirit of collaboration. Engineered for efficiency and scalability, the Cardano ecosystem will develop into the most complete cryptocurrency ever constructed.
Conceptual Innovation
- Privacy and regulation - The original Bitcoin blockchain was meant to be a way for individuals to transact directly and anonymously with each other outside the control of banks and governments. This guarantees privacy in financial dealings, a fundamental individual right. But full anonymity can be counterproductive, as can complete lack of regulatory oversight.
Today most blockchain projects look to further either the aims of privacy or of regulation. To be effective globally, we think our blockchain must ‘square the circle’ by finding the right mix of individual privacy protection and provision for regulatory control. - Governance - Public, decentralized blockchain projects rely on crowd-based governance models. This allows for democratic control of the network by its participants, which is essential to building truly decentralised economies. However, if they are not carefully designed, such governance can go awry.
Both the Bitcoin and Ethereum communities have experienced devastating schisms on the question of how to upgrade their networks – in Ethereum’s case already causing a split. The Cardano blockchain has an airtight governance model that allow the community to democratically take clear and binding decisions. - Funding - The Cardano blockchain has sophisticated maintenance and development needs and is able to adequately fund itself, both in terms of running costs and new investment.
The Token: ADA Voucher
Every blockchain project has a token of value commonly referred to as a cryptocurrency. Ada is the cryptocurrency on the Cardano blockchain. With Ada, holders can send value between friends, pay for a good or service, deposit funds on an exchange, or enter an application.
To perform a transfer on the settlement layer requires you own Ada, or acquire Ada through an exchange. It will also be the native token to be used in applications built on the computation layer.
The Wallet: Daedalus
Each cryptocurrency requires a “wallet” to store Ada. Typically this wallet is a software application that can be installed on any computer or smartphone.
Daedalus is a highly-engineered wallet with advanced security features that was developed by IOHK specifically for the Cardano blockchain and protects your assets with the most advanced cryptography. In the future, Daedalus will not only support Ada, but other cryptocurrencies such as Bitcoin, Ethereum Classic and many more.
Where To Spend Cardano?
ADA AVAILABLE AT THE LAUNCH OF THE CARDANO PROTOCOL
25,927,070,538 Ada were sold during the sale. An amount equal to 20% of the Ada Vouchers sold during the sale period, 5,185,414,108, Ada were generated and distributed to three entities of the Cardano ecosystem that are part of the Technical and Business Development Pool: IOHK, Emurgo and the Cardano Foundation. The total amount of Ada available at Launch will therefore be equal to 31,112,484,646 ADA.
ADA SUPPLY CAP
Ada is capped at an arbitrary 45,000,000,000 or forty-five billion Ada.
ADA TO BE ISSUED DURING THE OPERATION OF THE CARDANO PROTOCOL
The remaining Ada, 13,887,515,354, will be issued after launch through ‘minting’.
THERE WILL NEVER BE MORE THAN 45,000,000,000 ADA
BOOTSTRAP ERA (LAUNCH)
Cardano is currently in its bootstrapping phase. During this phase, fees are not being collected and no Ada is being minted. Fees from this phase will be collected in the future and they will be destroyed.
TREASURY
Cardano will have a treasury. The treasury will be endowed via some portion (yet to be decided) of newly minted Ada and transaction fees. The treasury shall be governed by Ada holders.
FEE (CURRENT CALCULATION)
Minimal fee = 0.155381 ADA + 0.000043946 (ADA/Byte) x size-of-transaction
Fee calculations and incentives are still an area of research under progress.
DENOMINATIONS
- 1 ADA = 1,000,000 Lovelaces
- 1 Lovelace = 1/1,000,000 Ada
- Ada has six decimal places.
- 1.000000 = 1 Ada
- 0.000001 = 1 Lovelace
In terms of money units there are two points of consideration. First in Japan, yen amounts are much larger, 10,000 yen is like the 100 dollar bill and factoring this into the units you go from 25 billion Ada to 250 million. Second Ada has six digits from the decimal not eight for Bitcoin. An Ada is a million Lovelaces (the smallest unit). Adjusting for this takes you to 2.5 million.
What Is Cardano Mining?
The Cardano Block Explorer can help you check transactions on the Cardano testnet, which is running now, as well as on the real version of the network, which is to be launched soon. (The Cardano Testnet is a pilot version of the network on which engineers are running tests to make sure it is operating smoothly and securely before the launch of the real network.)
- Overview - Table of Contents
- What Is Cardano?
- Getting Started With Cardano
- How To Get A Cardano Wallet?
- Cardano Resources
- How To Buy Cardano?
- How To Earn Cardano?
- Where To Spend Cardano?
- What Is Cardano Mining?
- Latest Cardano News
Developers are building the capabilities of the Cardano Block Explorer and it is planned to become a complete resource which will contain statistics, charts, and many more features.
On the home page, you will see a table showing the latest activity of the Cardano blockchain, headed “Last Slots”. This table shows you what epoch the blockchain has reached, the corresponding slot numbers in that epoch, and how long ago those stages were reached.
You can also see the number of transactions that occurred, the amount of Ada that was transacted, and the block size. You can click on the slots to find out more information about the blockchain at that particular stage.
The home page also features the “Transactions Feed”, a table at the bottom of the page showing the latest Ada transactions that have taken place. This table lists the transaction identity number, the date and time of the transaction, and the amount of Ada sent.
You can click on any transaction to reveal more details about it. You can also click on any address to see details of that address and a history of the transactions made to and from that address.
Latest Cardano News
Cardano marks its launch with Tokyo event

The technology was conceived in an Osaka restaurant more than two years ago and from that small beginning Cardano has been built into a leading cryptocurrency. The project has amassed a team of experts in countries around the world, has generated more than 67,000 lines of code, and has a strong and growing community in countries across Asia and beyond.
Along the way, Cardano has set new standards for cryptocurrencies with best practices such as peer review and high assurance methods of software engineering.
Cardano: A Blockchain with Privacy and Regulation

Blockchain is a potentially transformative technology. However current solutions are hampered by issues such as lack of regulatory oversight, experimental software with unproven security, poor governance that stifles scalability, and a lack of long-term planning for protocols.
With the imminent launch of the Cardano protocol and the completion of the first ever crowdsale to perform detailed compliance checks on its 10,000 individuals, Cardano aims to change this.
The Cardano project is a next generation blockchain, creating a new decentralised economy, and democratising finance in emerging markets. It addresses the need for regulatory oversight whilst maintaining consumer privacy and protections through an innovative layered architecture.
This software stack is flexible and scalable, developed with the most rigorous academic and commercial software standards. Cardano has a democratic governance model that will let the project evolve, and a visionary treasury system to fund it sustainably.
